Physical Hack, Insider Threat: Busted by Cortex XDR Managed Threat Hunting
This post is also available in: 日本語 (Japanese)
One day, a SOC analyst sits down at his computer with his morning coffee and opens the following message alerting him to a possible insider threat:
“Hello, my name is Alicia from the Cortex XDR Managed Threat Hunting (MTH) team. I’m investigating suspicious activity in your network and could use some assistance... To help our investigation, could you please check the following? ... ”
What is this?! Read on to learn about a sneaky insider attack and the service that discovered it with the latest story in our Busted by Cortex XDR series, featuring our Cortex XDR Managed Threat Hunting team!

This real customer story from an EMEA-based consulting firm took place in March before the COVID-19 pandemic hit, and began with an employee hacking his own laptop to obtain local admin credentials, using a technique called “Sticky Keys.” Here’s how the MTH team caught the employee, traced how the individual learned and built up the hack, and how the customer’s SOC team contained the attack:
![This screenshot of an email reads: Hello, My name is [OBSCURED] and I'm part of the MTH team. I'm investigating some activity in your network and can use some assistance. The activity in question can be viewed in XDR: XDR Activity. Overview of the activity: The activity appears to be a technique known as Sticky Keys. More information about this type of attack can be found here: [web address]. To help further our investigation could you please check the following: [Obscured details]. Thank you and please feel rfree to contact us if you have any questions or concerns. Very Respectfully, [Name Obscured], Cortex XDR Managed Threat Hunting Team](https://www.paloaltonetworks.com/blog/wp-content/uploads/2020/05/hello.png)
| “Sticky Keys”?
Windows contains accessibility features that may be launched with a key combination from the login screen. An adversary can replace these programs to get a command prompt – by default, these applications run under the system account, with administrative credentials. Two common accessibility programs are: 1. C:\Windows\System32\sethc.exe, launched when the shift key is pressed five times (Sticky Keys) 2. C:\Windows\System32\utilman.exe, the Windows application that is designed to allow the user to configure Accessibility options, such as the Magnifier, High Contrast Theme, Narrator and On Screen Keyboard when they press Windows + U on the login screen. |
Our customer’s SOC analyst clicked on the Cortex XDR Activity in Alicia’s email to get a picture of what she was referring to. Cortex XDR explained the suspicious activity in a simple graphical form:
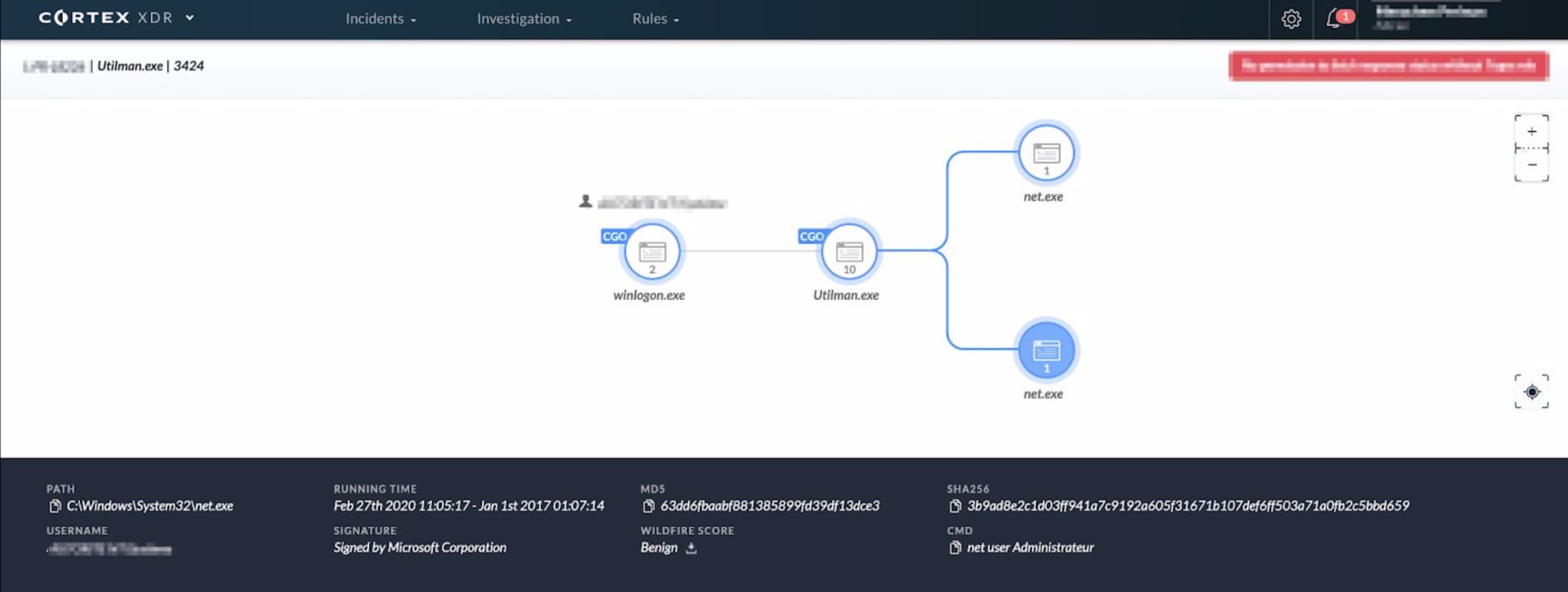
The customer’s SOC analyst quickly downed his coffee, rolled up his sleeves and grabbed his keyboard to confirm Alicia’s analysis. Alicia replied a few minutes later, explaining the nature of the threat and recommending steps for remediation. Here’s a screenshot of the actual response:
![This screenshot of an email reads: Thanks for getting back to me with the details, which confirmed what I was seeing. I'm just going to share with you some of my thoughts and recommendations being that I understand the Windows ecosystem and the technique. Utilman.exe is a Windows protected file and the only way to overwrite it would be to first disable windows system file checker. To achieve this one would need to be logged in ot the PC and typically is performed manually. The modification is done in the registry or direct calls into [obscured]. From the activity I would treat the host as fully compromised and from the commands issued assume that local creds were taken. Hopefully the local creds aren't domain creds? Recommend changing the users account information. Attackers typically do this as a 2nd stage access to a network in the event their initial access is lost. Thanks for the help and please let me know if you have any questions. [Name obscured]](https://www.paloaltonetworks.com/blog/wp-content/uploads/2020/05/morning.png)
The “Sticky Keys” technique triggered our MTH team’s attention as part of looking for signs of admin credentials harvesting. Utilman.exe is a Windows protected file and the only way to overwrite it would be to first disable the Windows system file checker, or do it without the operating system running.
Unfortunately...
The employee had already gained local admin creds and continued his attack through the command shell. The question now: What did the employee do with those creds? Before we share what happened in the heat of the moment, let’s take a break instead and learn who Alicia is.
Who’s Alicia?
Alicia is an expert in hunting and collecting threats, and in reverse-engineering malware using code analysis. Her team runs in-depth research to gain insight into techniques that threat actors use to compromise entire organizations. Her goal is to provide context, explain the nuts and bolts of attacks, who’s executing them and why they do so. What gets Alicia going is to empower SOCs to better defend their companies.
The Hack
Back to the story: Cortex XDR’s endpoint agent logs signaled that the employee obtained admin credentials to his laptop (which, for the record, happened without the company’s permission). He replaced utilman.exe on his computer with cmd.exe, the Windows command shell, which triggered an alert that Alicia picked up and connected with a couple of commands that the employee ran right after. Until Alicia’s email arrived, the customer’s SOC analyst was unaware of the situation. Without the Managed Threat Hunting service, this could have come across as a few unrelated activities, and could have ended up as a missed attack.
But Why?
The MTH team continued to investigate Cortex XDR network and endpoint logs and found that the employee ran commands to reset the local admin’s password and to list local user accounts that were previously logged into his laptop.
Alicia explains that attackers can use a password reset to gain access to accounts. They do this to regain network access when they’ve lost it over the course of carrying out an attack. The employee may have been on the network for a while.
In the best-case scenario, the employee turned to the dark side only to “level up” his laptop for innocent, work-related tasks.
Alternatively, Alicia explains that the enumeration of local user accounts is a sign of an attempt to gain access to other users’ accounts, and possibly even to domain admin credentials. The former can grant access to confidential information, such as source code or sales results, while the latter can take the company’s computer network down. When a user logs in to a PC, the login credentials get cached in Windows. With local admin rights, attackers can enumerate that cache and, with various techniques, operate on behalf of those accounts – even on behalf of domain admin accounts – to access network resources.
How Could He Do It as a Regular User?
The employee was a regular user and shouldn’t have been able to replace utilman.exe with the command shell. The Windows operating system deploys several protective mechanisms to prevent this abuse. One mechanism is that the application must reside within the System32 folder (which is why cmd.exe was used, and not other applications). Another is that the change can only be made by an administrator.
Alicia kept investigating. She searched the internet, network and endpoint logs for clues to help the customer’s SOC analyst understand how the user could escalate his privileges to be an admin. She eventually found that the employee physically attached a USB stick to his laptop, restarted the computer, launched a live Linux distribution from the USB stick, mounted the Windows partition and finally copied cmd.exe onto utilman.exe, overriding Windows’ operating system file protection while Windows wasn’t running. The employee then reset the system again, removed the USB stick, booted back the Windows partition, pressed Windows + U on the login screen and suddenly faced a blank command window, running under the highest local privileges, ready to execute his commands.
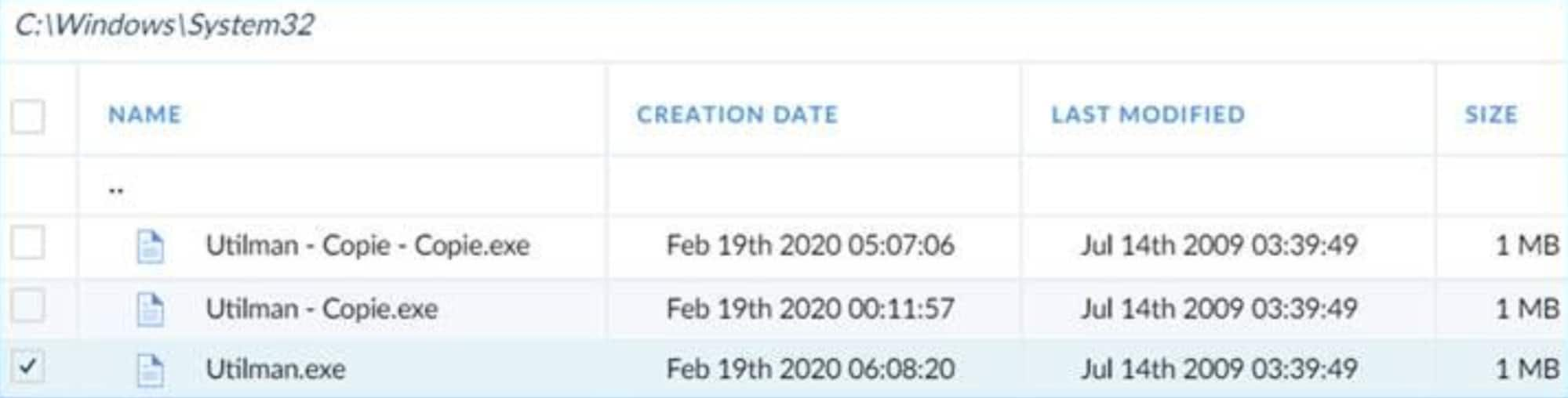
Busted.
Following these insights by Alicia, the customer’s SOC analyst confirmed the employee’s activities by connecting to the laptop using Cortex XDR Live Terminal. The customer’s SOC analyst took the laptop down, disabled the employee’s account and initiated the necessary HR actions that same day. Alicia had found a threat, helped the customer’s SOC analyst find the root cause, recommended remediation action and moved on to the next threat in the world. The customer’s SOC analyst learned a new trick and, thankfully, got out of this trouble before it turned into a disaster. What happened with the employee and how far he got before they caught him remains a mystery. What we know is that they caught him early enough to not read this story in the news as a data breach, a long outage or a copyright infringement case – and that’s what matters.
The CSO remembers the next day’s triage with a sense of a “perfect day,” feeling confident about his SOC team and how the Cortex XDR Managed Threat Hunting team helped protect his company.
Best Practices to Protect Against Insider Threats
Insider-caused security incidents – whether due to malice or negligence – are a pervasive problem for organizations and can be hard to prevent without disrupting the ability for employees to do their jobs. Ponemon Institute has found that the percentage of insider incidents has increased by 47% since 2018, and the cost has increased by 31% over the same time period. Here are some steps that your security team can take in order to minimize the chances of an insider threat like the one described above:
- Identify and manage critical or sensitive assets. The development of workplace technologies has allowed for rapid collaboration and access to information, but also allows for those assets to be more easily exfiltrated. Security teams should have a complete account of an organization's assets along with access management tools and policies to defend against an insider threat.
- Document and enforce security policies. At times, employees may become unintentional insider threats due to unclear or inconsistent security policies regarding an organization's assets. Organizations must clearly outline acceptable use of assets, use of privileged accounts, ownership of intellectual property and other similar topics. Along with the policies, organizations should be able to provide clear justification and reasoning behind each policy.
- Create a response strategy for insider threats. While we may not be able to completely eliminate insider threats, an organization can construct strategies to rapidly respond to insider threat incidents, thus helping to minimize damage to the organization should one occur. These strategies may involve creating a working group across departments and functions or having dedicated personnel to handle insider threat incidents.
Sharpen Your Threat Hunting Skills
On June 23, we’ll be holding the “Inside The Hunt” virtual summit, dedicated to threat hunters everywhere. We’ve gathered some of the best and the brightest threat hunters and industry experts from around the world to share best practices on threat hunting strategies, techniques, challenges and technologies. Learn new tips that will help you improve your threat hunting practices right away and participate in trivia to win prizes. Register for “Inside the Hunt” for free!
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.