2021 Gartner Market Guide for CWPP: Key Takeaways
Updated July 16, 2021
Cloud native development relies on workloads spread across any number of compute options – virtual machines (VMs), containers, serverless and many points in between. These components which make up cloud native applications can be created and spun down in a matter of hours or even minutes – they are surprisingly ephemeral.
Moreover, protecting these workloads can be difficult. Discovering when they have been created, determining who or what is accessing them and figuring out whether they are configured correctly is a monumental task not suited for manual security work. That's why the market has seen an influx of platforms specially designed to protect them. These so-called cloud workload protection platforms (CWPP) are evolving almost as quickly as the workloads themselves, and understanding key functionality can be overwhelming.
Gartner recently released its 2021 Market Guide for Cloud Workload Protection Platforms, which has annually examined the latest developments in cloud native infrastructure security and offered recommendations on how enterprises should protect these components and the continuum of compute options, including VMs, containers and serverless workloads.
Palo Alto Networks is proud to be included by Gartner as a Representative Vendor for CWPP.
What Is a Cloud Workload?
First, it may be helpful to understand what these platforms can actually protect. A workload can be broadly defined as the resources and processes needed to run an application. A cloud workload typically includes an application, but it also involves things like data served to and generated by the application, as well as network resources required to connect users to the application or to connect different parts of the application together.
Most organizations' workloads now typically span multiple cloud service providers (CSPs) and compute options, and a majority of organizations intentionally choose multiple types of infrastructure offerings based on business needs. According to Gartner, “Workload protection must span virtual machines, containers and serverless workloads in public and private clouds. Security and risk management leaders should use this Market Guide to understand the need for protection that spans development and runtime and includes cloud security posture management.”
We've talked for a while now about how each infrastructure offering comes with individual configurations and security requirements, which we highlight in our whitepaper titled the Continuum of Cloud Native Topologies.
What Is a Cloud Workload Protection Platform?
Second, Gartner defines cloud workload protection platforms (CWPP) as "workload-centric security products that protect server workloads in hybrid, multicloud data center environments." Or as we simply say, these platforms help enterprises protect workloads. They also offer greater visibility and control over them, regardless of their location.
These platforms need to help security leaders continuously assess risk across cloud native architectures and identify vulnerabilities and misconfigurations before deployment to runtime to minimize runtime problems. These platforms span CSPs to provide greater assurance with less manual effort.
Protection Needs to Span the Entire Application Lifecycle From Build to Runtime
We've seen that the diffusion of DevOps methodologies has led to the increasing granularity of workloads. DevOps intentionally uses small, frequent iterations, where deployments happen multiple times a week or even multiple times a day.
In order to protect these increasingly ephemeral workloads, security and risk management leaders need to understand what workloads are running where, and Cloud Workload Protection Platforms help them do that.
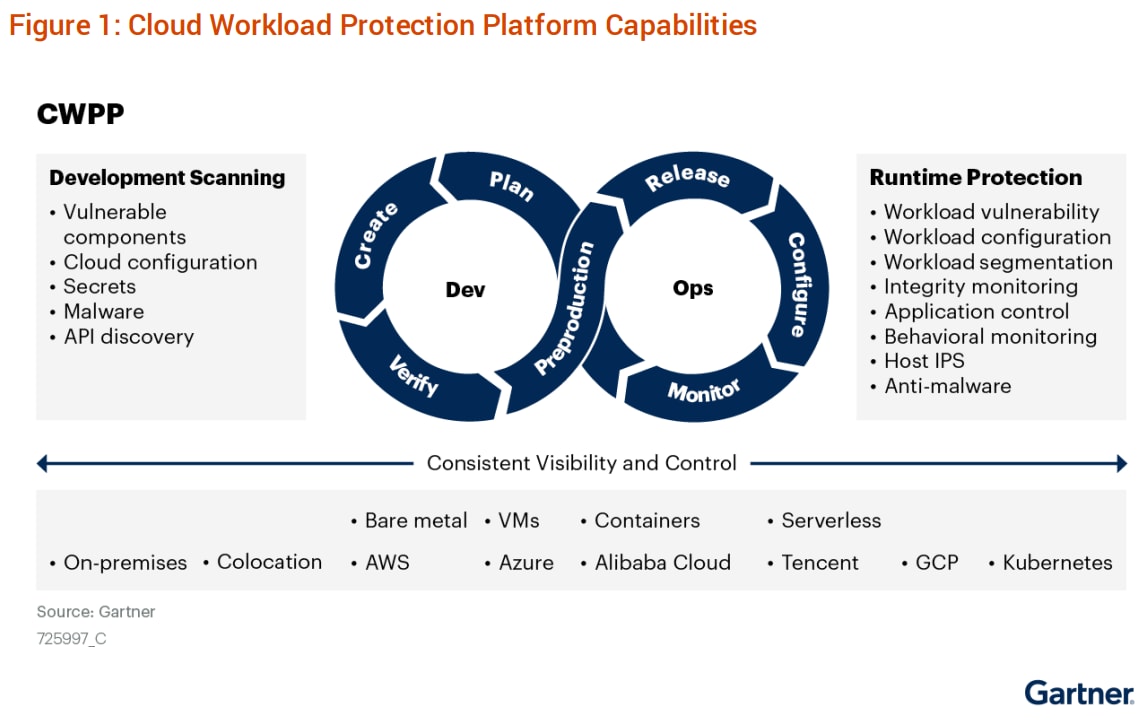
Security controls need to support public, private and hybrid clouds, while also combining full stack runtime protection with integrated DevOps security. These capabilities include vulnerability management, compliance, runtime protection and application control, and other key security controls highlighted by Gartner.
Recommendations for Security and Risk Management Professionals
The report highlights key recommendations organizations should consider for securing their cloud infrastructure. Palo Alto Networks has chosen to emphasize the following for a full lifecycle, full stack security approach:
- Implement a CWPP offering that protects workloads regardless of location, size, runtime duration or application architecture.
- Secure workloads earlier by extending workload scanning and compliance efforts into development (DevSecOps), especially for container-based and serverless function platform as a service (PaaS)-based development and deployment.
- Consolidate CWPP and CSPM strategies over the next 12 to 24 months to reduce costs and complexity and identify risks better.
As an integrated Cloud Native Security Platform, we believe Prisma Cloud aligns strongly to this consolidation trend across CSPM and CWPP.
To read the report in full, including further in-depth exploration of these best practices and recommendations, download your copy of “Market Guide for Cloud Workload Protection Platforms.”
Gartner, Market Guide for Cloud Workload Protection Platforms, Neil MacDonald, Tom Croll, 12 July 2021
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from https://start.paloaltonetworks.com/gartner-market-guide-cwpp.html.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.