5 Reasons Why Threat Intel Management Needs to SOAR!
Threat intel management has been an unsolved puzzle for a long time. Security analysts and threat hunting teams still struggle to efficiently and confidently act on relevant indicators of compromise using disjointed threat intel feeds, tools and processes. Threat intel platforms have proven to be of little use to analysts, who still spend time collecting feed data from various sources, manually entering it into centralized tools for reference, and eventually processing and pushing the relevant data to third-party enforcement tools for action. This tedious process drains precious resource time and increases mean time to response (MTTR). Faster, more scalable systems are badly needed by the already-stretched teams responsible for defending against highly sophisticated adversaries.
As security orchestration, automation and response (SOAR) platforms are designed to connect disparate systems together and automate manual processes, extending SOAR to provide native threat intel management functionality is a natural progression that solves a lot of these issues. According to Gartner’s Market Guide for Security Orchestration, Automation and Response Solutions, “A large number of security controls on the market today benefit from threat intelligence. SOAR tools allow for the centralized collection, aggregation, deduplication, enrichment of existing data with threat intelligence and, importantly, conversion of intelligence into action.”
Here are 5 reasons why extending SOAR capabilities to threat intel management can help fix broken threat intel management processes:
1. Get full control of your threat data
Security analysts often lack control over threat intel feeds, forcing them to manually tune and score indicators to match their environment. To understand and explain why exactly a particular indicator matters, analysts spend a lot of time gathering context around threat data, trying to make sense out of it. Way too much of this process is complicated and manual: defining and identifying threat data, applying those indicators across their various systems, extracting unstructured threat data from multiple sources, and understanding the specific contexts and timeframes in which each indicator is relevant (as the dynamic nature of threats means that observables may be relevant in one instance but not the next). To ensure accuracy, applying indicators in the right timeline is essential. Gaining control over threat data is a powerful step toward ensuring the right outcomes.
Marrying threat intelligence with SOAR – as Palo Alto Networks has done with Cortex XSOAR – provides complete control over threat data management. Cortex XSOAR ingests both structured and unstructured threat intel feeds and allows security teams to automate a lot of what is done with that data in flexible ways, allowing them to perform multiple operations efficiently from a single console. Threat analysts have full control over the management of threat data, plus the ability to add additional context. They can slice and dice data where they need to, bringing their experience, values and judgement to programmatically build countermeasures across the enterprise.
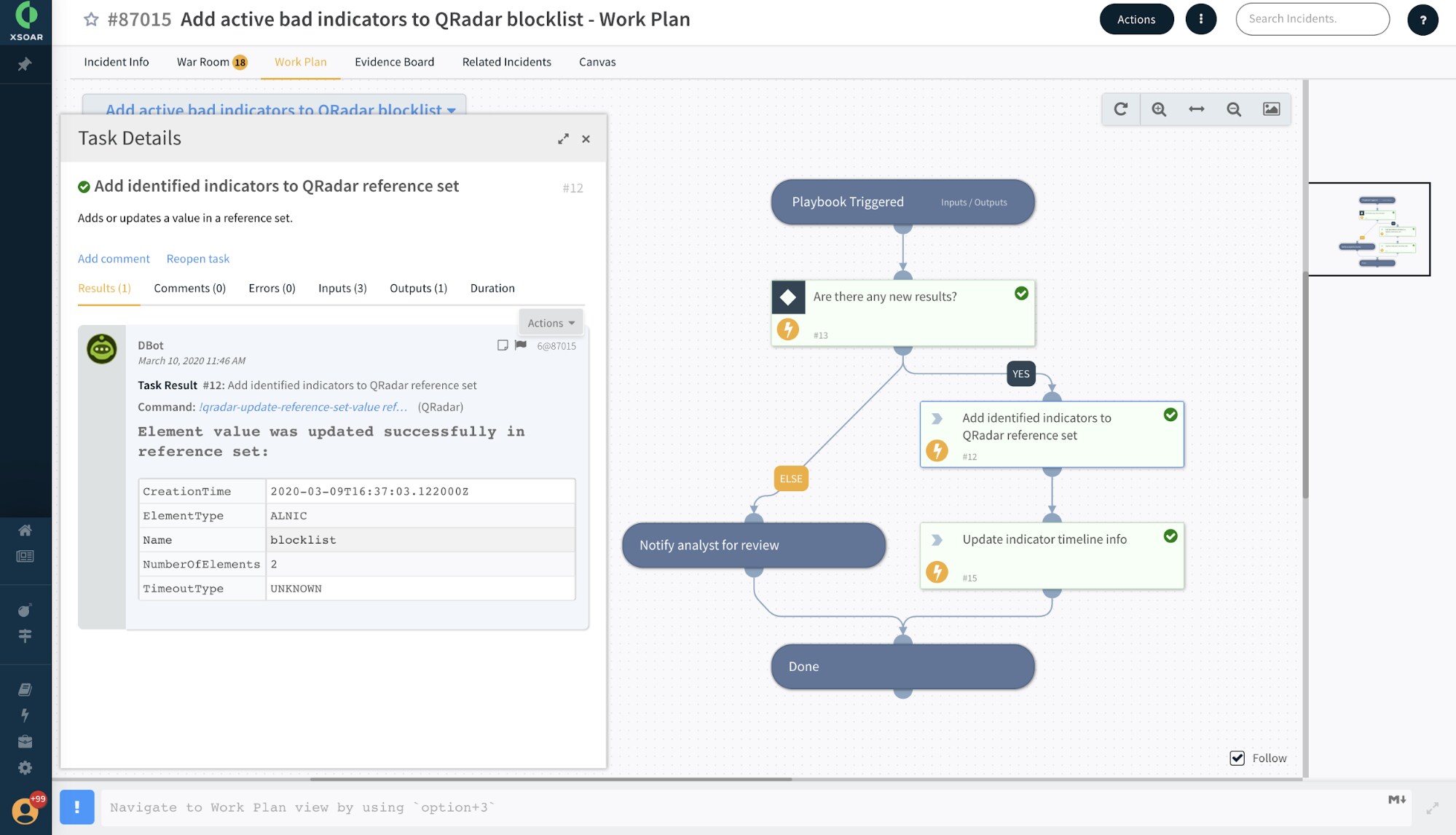
The extremely modular nature of XSOAR helps analysts to create custom layouts and response actions. For viewing data, Cortex XSOAR users can not only build flexible widgets to view the data as they’d like, but they also have access to DBot, the security bot that can fetch data from different sources and present it on the console for instant viewing. The platform links all these things together in a relational way that is visually represented to show how indicators are related and which incidents they are associated with, which helps security teams bring accuracy and speed up their response operations.
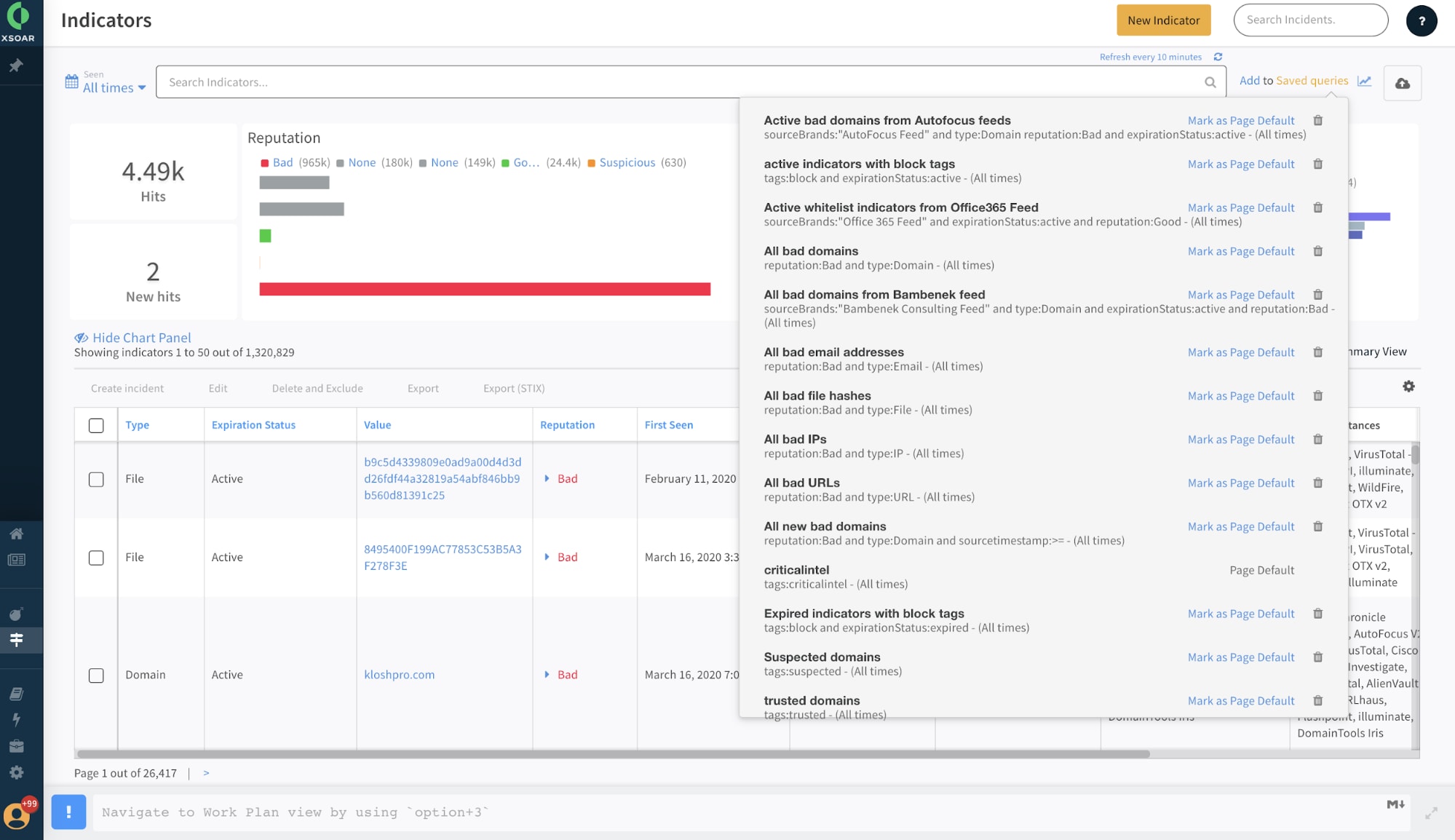
2. Use automated playbooks to unify threat feed ingestion, indicator enrichment and incident management workflows, bringing machine speed to SecOps
The siloed-yet-dependent nature of threat hunting operations and incident management wastes time and makes it more difficult to meet SLAs. Use cases such as incident prioritization based on threat intel and retroactive alerting are often impossible to implement in a way that is both accurate and scalable given the number of incidents and indicators.
Cortex XSOAR playbooks can unify threat intel feed ingestion, indicator enrichment, validation and incident management processes to speed up security operations. Playbooks are flexible, so analysts can choose to drive them using either incidents or indicators. Threat intel teams can automate their repetitive tasks, including indicator correlation across tools, validation, threat impact assessment, threat hunting operation, incident management and so on. The flexible workflows open up doors to new possibilities while dramatically reducing response times.
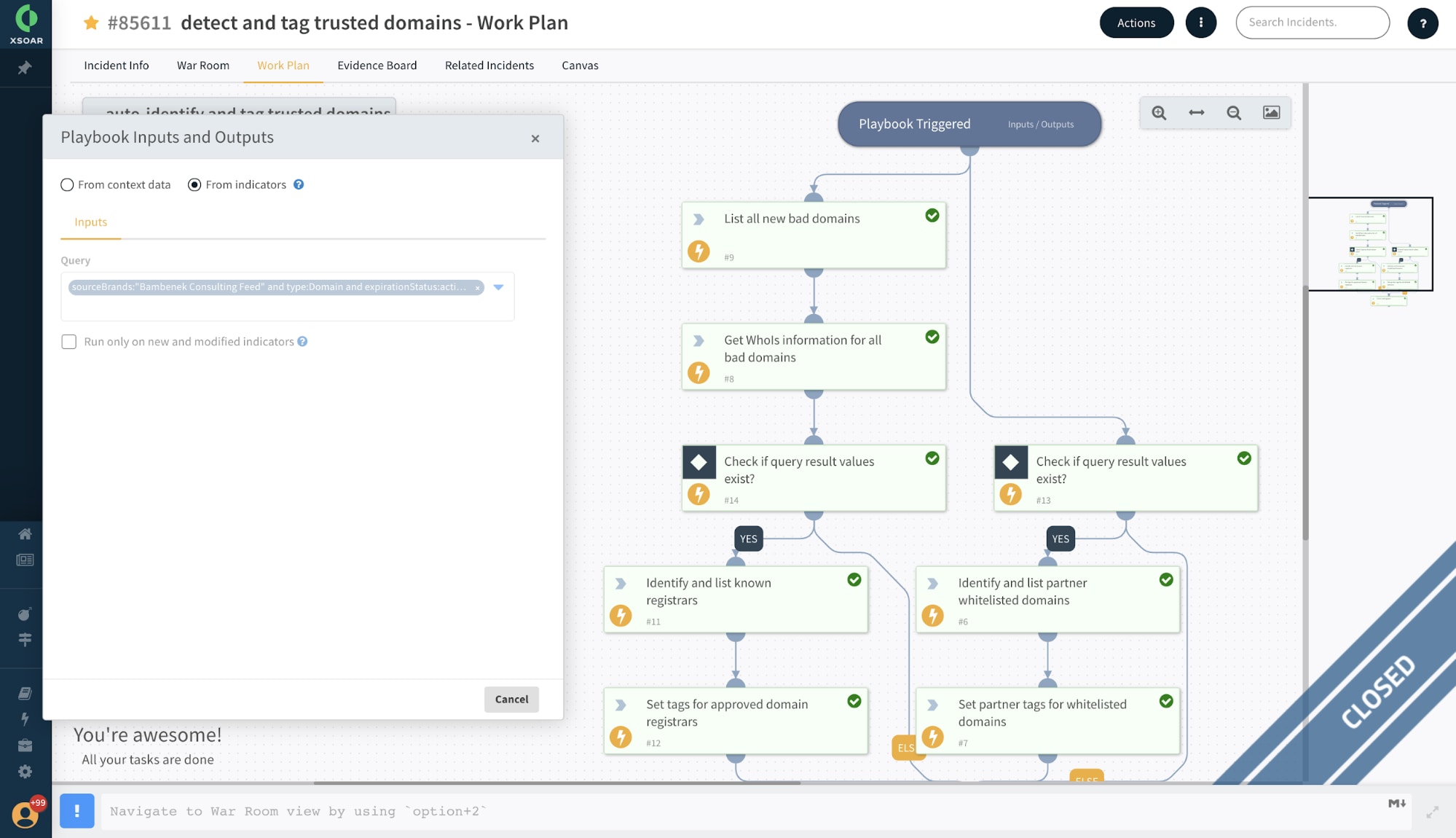
3. Gain access to current indicator timeline information
Actionable threat intelligence must be complete and up to date. This is crucial for analysts, who must make calculated decisions during each stage of the threat intel lifecycle process.
Cortex XSOAR ingests rich threat intel feeds from multiple sources and automatically correlates them with indicator information extracted from alerts and incidents. The platform tracks each individual indicator throughout its lifecycle and presents the timeline information for each indicator. Analysts can have confidence that they always have access to the most up-to-date information about each indicator during the threat investigation process, including the timeline, reputation, source details, related incidents, tags and expiration status. The sheer ability to automatically annotate individual indicator data based on playbook actions is a huge differentiator. All this helps analysts to keep track of indicators of interest and manage the lifecycle of particular threats.
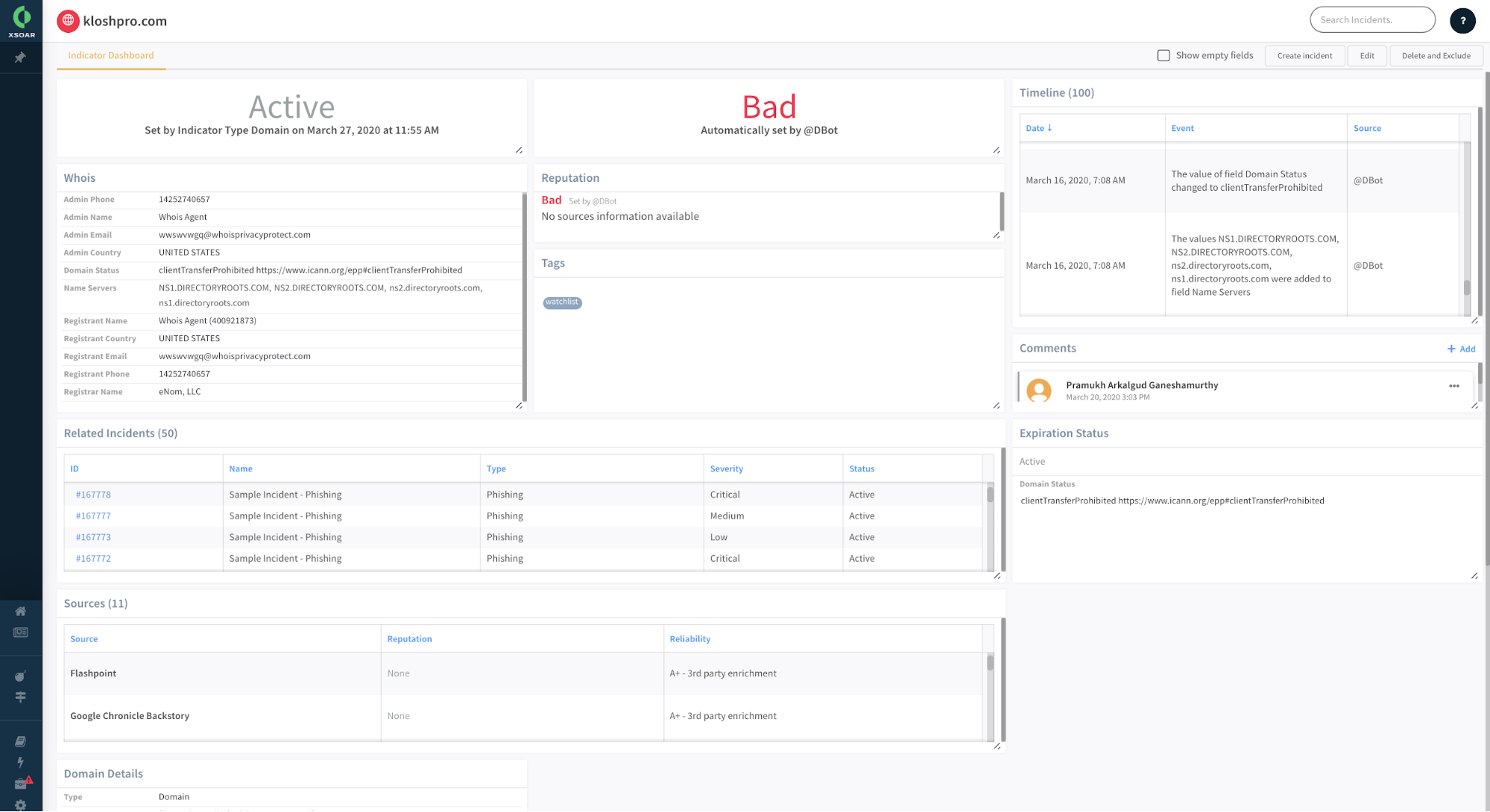
4. Bring your own custom scoring logic to boost confidence on threat data
Threat intel teams often lack the ability to bring their own custom indicator scoring logic into their threat intel operations. Most threat intel platforms have static rules of confidence, obscuring visibility into the scoring logic. This lack of visibility and control over indicator scoring mechanisms reduces confidence in the threat intel and inhibits security teams from taking decisive response actions.
With Cortex XSOAR, analysts can now bring their own custom scoring logic with threat intel playbooks to set new scores for threat intel indicators based on custom logic. Analysts can also create playbooks to implement their organization’s exact threat management processes to determine the right confidence levels to automatically respond on the actionable threat intel. The indicator scoring process itself might include performing several checks for establishing trust and validation. Cortex XSOAR automatically links the results to the threats they represent and notifies the analysts to approve response actions. In another scenario, analysts can configure playbooks to identify when new reports of relevant activity have been received and tune out the noise of irrelevant reports. Using SOAR to manage threat intelligence, security teams can readily ingest threat intel feeds with much higher confidence.
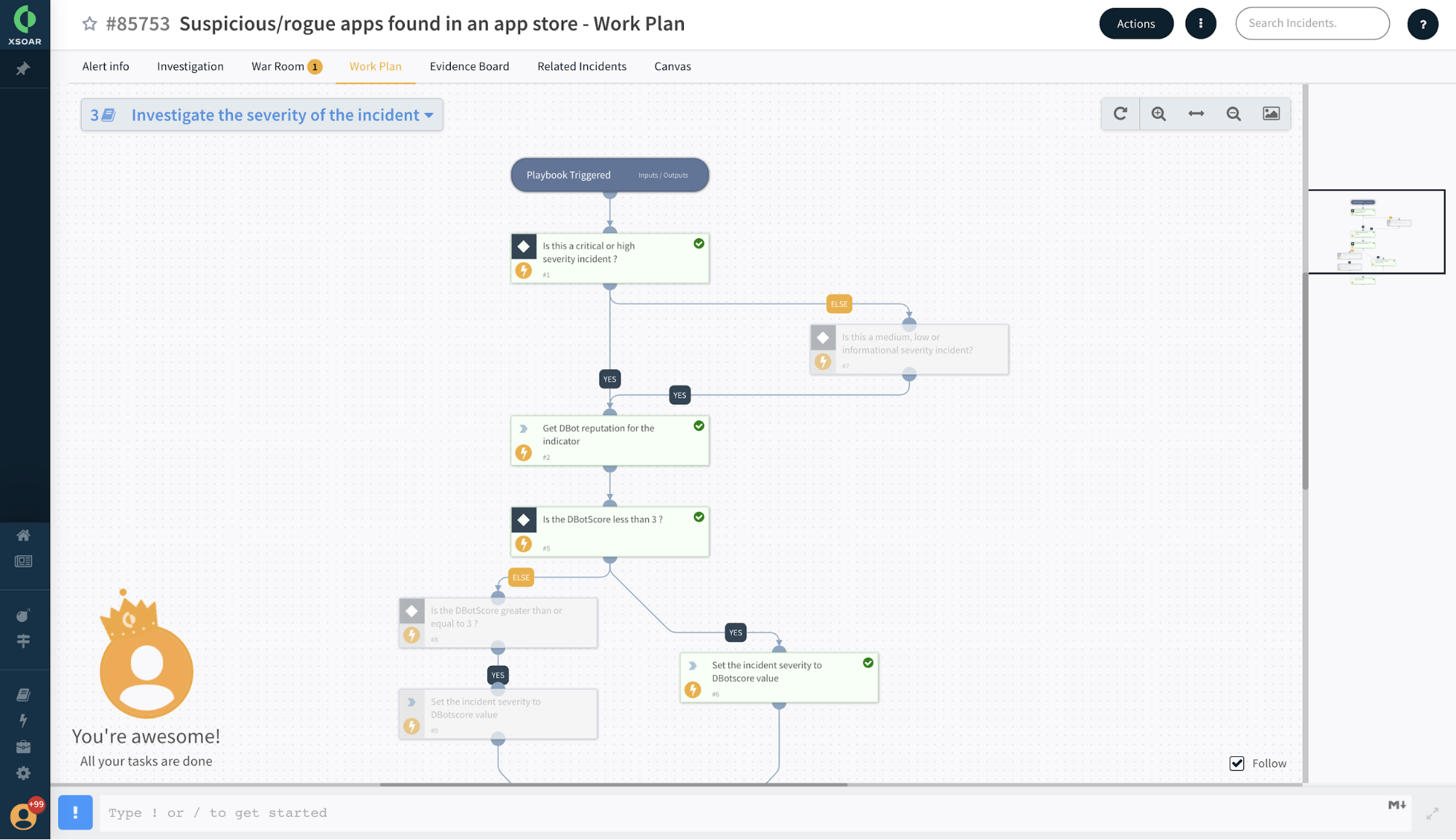
5. Put threat intelligence into action automatically. Close the loop between threat intel generation, indicator sharing and response.
Putting threat intel into action is a highly manual, repetitive and time consuming activity. Threat intel and incident response teams lack the ability to act on threat intelligence accurately and at a high volume due to silos between threat intelligence tools, teams and enforcement points.
Cortex XSOAR closes the loop between threat intelligence generation and response automation. It contextualizes threat data at scale so that it can be applied operationally in the right way. This removes the need for threat analysts to curate millions of indicators and brings the ability to apply similar logic for response automation to a wider set of threat intel at the same time. Analysts can automate threat intel sharing and enforcement across a number of enforcement points, such as firewall external dynamic lists and security information and event management (SIEM) blocklists. For example, if a darkweb report confirms certain users were compromised, analysts can automatically have the user control enforce two-factor authentication on those users. Similarly, analysts can have a whitelist or a blacklist of indicators pushed automatically to the firewall or a SIEM watchlist. Cortex XSOAR brings full threat intel ingestion into the platform and ties it with a completely customizable workflow to help speed up SecOps. One of the key pillars of the platform is War Room ChatOps functionality, which allows different security teams to collaborate in real time. This is of immense help during crisis times such as the COVID-19 shutdown, when remote analysts can still continue to collaborate, take response actions and maintain service level agreements. This is a clear game changer for security operations and threat hunting teams in their struggle to reduce MTTR.
Learn more about Cortex XSOAR.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.