3 SecOps Strategies To Enable Your Smart People To Focus on Smart Things
This post is also available in: 日本語 (Japanese)
This blog is the third in a series based on our book, “Elements of Security Operations,” a guide to building and optimizing effective and scalable security operations. Download a free copy today.

Presumably, you hire smart people because you want them to spend their time doing smart things. But what happens when your processes are broken, outdated, poorly defined or unscalable? Your talented employees are forced to waste energy overcoming these challenges rather than spending it on the activities for which they provide unique value. The key to solving these problems is implementing better SecOps strategies.
This is a pervasive challenge in the average enterprise security operations center (SOC), where alert-generating security tools have multiplied way too fast for anyone to meaningfully integrate them, while at the same time threats have gotten more sophisticated and harder to detect. Analysts toil away to manually identify, validate and remediate an endless flow of alerts. This is not maximizing their job satisfaction, their efficiency nor their overall impact on your security posture.
Here’s what the typical SecOps analyst time allocation looks like today relative to the ideal state:
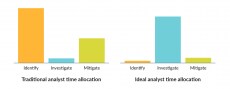
The majority of an analyst’s time is spent weeding through false positives and low-fidelity alerts to identify and triage malicious threats. A lot of time is also spent in threat mitigation. Some of this is due to a lack of automation. Other difficulties are introduced by inefficient interfaces with teams and tools outside of the security operations organization that need to be involved in halting the attack. Proportionally little time is spent actually investigating the root cause and impact of a confirmed security incident, and even less time is spent on operational improvement. These latter two areas are where human analysis is most important, and where your talented analysts can have the greatest impact.
Smarter SecOps Strategies
Enterprises need to fix this. We need to let smart people do smart things. Here are three strategies to get you started:
1. Focus on Prevention-Based Architecture.
Preventing an attack outright is always the ultimate security outcome. Prevention architecture may exist outside of the SecOps function itself, but it affects the efficiency and efficacy of achieving the SOC mission. Without a prevention-based architecture, analysts can be overwhelmed with false-positives and low-fidelity data. This can result in detuning sensors and ignoring alerts. Analysts may begin to rush investigations or overlook making updates to controls, which amplifies the problem. A properly implemented prevention-based architecture ensures that machines are used for what they are good at – events – and people can focus on what they are good at – situations.
A prevention-based architecture cuts down on the noise in the SOC and is comprised of:
- Consistent protection across the network, cloud and endpoints.
- Centralized management of security controls and devices to provide consistency and reduce administration time.
- Automated threat prevention that can update security controls in minutes, not days.
- Prevention based on data, assets, applications and services (DAAS) to move controls closer to critical assets and to reduce policy and rule maintenance.
2. Automate Repetitive Processes.
Prevention of known threats isn’t the only function that should be automated by your security tools. Any process that is repetitive and/or transactional and can be automated should be automated. This is one of the absolutely key things that we work with our clients on, and it is critical to overcoming alert fatigue and product/data silos.
Automation can be driven by rules as well as machine learning, and it relies on several primary tools:
- XDR for automated alert grouping, enrichment and prioritization, among other things.
- Security orchestration, automation and response (SOAR) tools that run playbooks to aggregate threat intelligence, open tickets, route issues to the appropriate person and execute remediation through integration with different point tools, among other things.
While analysis and investigation of an incident is a key human function, machine learning and automation can be built into and around these processes to assist in a variety of different ways to accelerate investigations, increase confidence and decrease administrative burden.

3. Structure Tasks to Avoid Burnout.
Security operations staff are prone to burnout due to console fatigue and extreme workloads. To avoid this, team members should be assigned different tasks throughout the day. These tasks should be structured in a rotation and may include:
- Shift turnover stand-up meeting (beginning of shift).
- Event triage.
- Incident response.
- Project work.
- Training.
- Reporting.
- Shift turnover stand-up meeting (end of shift).
Another tactic to avoid burnout is to schedule shifts to avoid high-traffic commute times. Depending on the area, 8 a.m.-5 p.m. may line up with peak (vehicle) traffic patterns. Shifting the schedule by two hours could reduce stress on the staff.
While these three tips are great starting points, there are many more considerations covered in the Elements of Security Operations book that will help you get the most out of your security resources. Join us for our “4 Life Hacks to Love Your Security Job” webinar on Feb. 25 to hear me and Kasey Cross discuss additional strategies to improve SecOps employee utilization and satisfaction.
We’ve embraced each of the above concepts to develop a lean, efficient and constantly improving security operations center for our own company, with analysts who are able to contribute to meaningful work regardless of seniority. To see how these concepts work in practice, read this case study on the Palo Alto Networks SOC. This case study walks through our SOC structure, philosophy and strategies, and describes the implementation processes for Cortex XDR and Demisto (SOAR) to improve our visibility and automation.
Get Hands-on with Cortex XDR

Interested in playing around with XDR while learning new tips for prevention, detection, investigation, and threat hunting? Attend one of our free investigation and threat hunting virtual hands-on workshops and get great insights, SecOps strategies and hands-on experience from the comfort of your desk.
Watch for future posts in Kerry Matre’s series on “Elements of Security Operations.”
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.