Protecting Endpoints From Day One
Deploying and managing endpoint protection shouldn’t be difficult. However, customers of traditional endpoint protection products complain about day-to-day management, database maintenance, agent updates, and constant tuning to eliminate false positives and keep resource utilization in check. Worst, even with all this work, endpoints still get compromised.
A customer who was evaluating Traps put it into “listen mode” to see if it would catch anything the customer’s existing endpoint protection product could not. Within minutes of deploying agents, a domain controller lit up the Traps management service console with alerts. When the incident response team pulled up the console, they immediately identified a piece of targeted malware that had been running on that server for some time. This was an eye opener, and the customer immediately realized the simplicity and power Traps offers, even from day one.
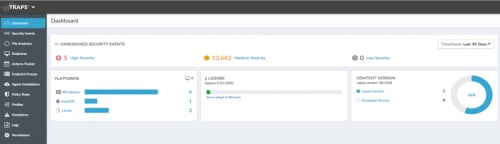
Traps Management Service
As new malware variants pop up around the globe, and as new software bugs and vulnerabilities are discovered, it can be challenging to ensure your endpoints remain secure. With the cloud-based Traps management service, you save the time and cost of building out your own global endpoint security infrastructure. Its simplified deployment requires no server licenses, databases or other infrastructure to get started, enabling you to start protecting your endpoints from day one.
Palo Alto Networks deploys and manages the Traps management service security infrastructure globally to manage the endpoint security policy for local and remote endpoints, ensuring the service is secure, resilient, up to date and available when you need it. This allows you to focus on defining the polices to meet your corporate usage guidelines instead of deploying and managing the infrastructure.
Traps management service comprises the following components:
- Traps management service web interface is a cloud-based security infrastructure service designed to minimize the operational challenges of protecting your endpoints. From the Traps management service, you can manage your endpoint security policy, review security events as they occur and perform additional analysis of associated logs.
- Traps agents protect each local or remote endpoint. The agent enforces your security policy on the endpoint and reports when it detects a threat. Agents communicate securely with Traps management service using Transport Layer Security 1.2.
- Logging Service is a cloud-based logging infrastructure that allows you to centralize the collection and storage of Traps agent logs, regardless of location. Traps agents and Traps management service forward all logs to the Logging Service. You can view these logs in Traps management service, and with the Log Forwarding app, you can forward logs to an external syslog receiver.
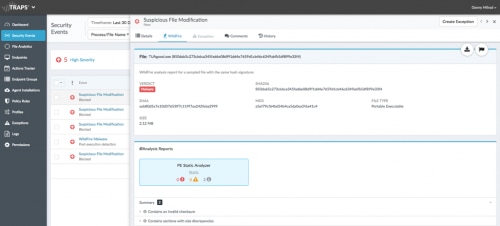
Integrated with Traps, WildFire malware prevention service identifies previously unknown malware and generates signatures that Palo Alto Networks next-generation firewalls and the Traps management service can use to detect and block the malware. When a Traps agent detects an unknown sample, Traps management service can automatically forward it to WildFire for analysis. Based on the properties, behaviors and activities the sample displays when analyzed and executed in the WildFire sandbox, WildFire delivers a verdict: benign, grayware, phishing or malicious. WildFire then generates signatures to recognize any newly discovered malware and makes the signatures globally available in as few as five minutes.
Traps management service provides out-of-the-box protection for all registered endpoints, with a default security policy for each type of platform.
Traps Security Profiles
Out of the box, Traps management service provides default security profiles you can use to begin protecting your endpoints from threats immediately. Although security rules enable you to block or allow execution of files on your endpoints, security profiles help you customize and reuse settings across different groups of endpoints. When Traps detects a behavior that matches a rule defined in your security policy, it applies the security profile attached to the rule for further inspection. You can enjoy immediate protection from multiple security profiles:
- Exploit profiles block attempts to exploit system flaws in browsers and operating systems. These help protect against exploit kits, illegal code execution, and other attempts to exploit process and system vulnerabilities.
- Malware profiles protect against the execution of malware, including Trojans, viruses, worms and grayware. Malware profiles serve to define how to treat behavior common with malware, such as ransomware or script-based attacks, and how to treat known malware and unknown files.
- Restrictions profiles limit where executable files can run on an endpoint. For example, you can restrict files from running from removable media or specific, local folders.
- Agent settings profiles let you customize settings that apply to the Traps application, such as the disk space quota for log retention. For Mac® and Windows® platforms, you can also customize user interface options for the Traps console, such as accessibility and notifications.
Conclusion
Security built solely to protect virtual endpoints often lacks the broader contextual intelligence critical to effective enterprise security architecture. Integrated threat intelligence, including data on the tactics, techniques and procedures of new and previously seen cyberattacks, is often critical to successfully defend systems and networks.
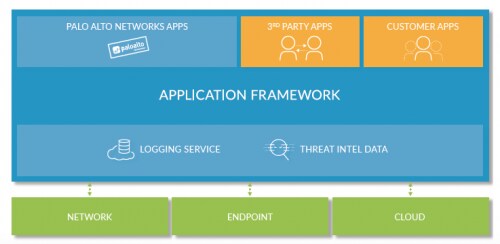
As an integral part of the Palo Alto Networks Security Operating Platform, Traps prevents cyberattacks automatically and in real time, regardless of the nature of the endpoints and the systems you have deployed. In concert with WildFire, Traps and the entire Security Operating Platform benefit from increased contextual visibility into – and protection against – correlated threat actors and campaigns, wherever they may try to attack.
Customers depend on Traps to ensure endpoints are protected, whether online or off, on-site or remote. IT teams must be able to confidently apply policies that control access to critical resources, and you need confidence in the integrity and configuration of the devices being used to connect to your network, whenever and wherever that may be. Protection cannot depend on full-time network access – it should just work, out of the box, from day one.
Watch the webinar “5 Endpoint Protection Best Practices” to learn the essential requirements for endpoint protection, and how Traps advanced endpoint protection is simple to deploy and manage, providing a prevention-first approach that protects endpoints from malware, exploits and ransomware.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.