
This post is also available in: 日本語 (Japanese)
What a difference a year makes! As the dominant exploit kit (EK) in our current threat landscape, Rig EK has gone through significant changes. How much has Rig EK changed? In order to find out, we compared activity levels, malware payloads, and network traffic characteristics from January of 2017 with January of 2018. The contrast is striking.
Activity Levels: A Dramatic Drop
Since 2017, Rig EK has remained the most significant player in the EK market, and it still accounts for the vast majority of EK traffic we currently discover. However, overall EK activity dramatically declined during 2017. We already reported a significant decline in Rig EK that began in April 2017. By the fourth quarter of 2017, overall EK activity levels fell even further, declining 31 percent from the previous quarter.
But how dramatic is the change from January 2017 compared with January 2018?
An easy way to gauge Rig EK activity is to search AutoFocus for items tagged RigEKFlashContainer seen through web traffic over port 80. In this search we omitted various anomalies such as results associated with malware samples submitted to places like VirusTotal or VirusSign. Using these criteria, we compared January of 2017 with January of 2018. For January 2017, we verified 812 sessions with hits on RigEKFlashContainer. In January 2018, using the same search criteria, we found only 65 sessions. That represents a 92 percent decrease in Rig EK from January 2017 to January 2018.
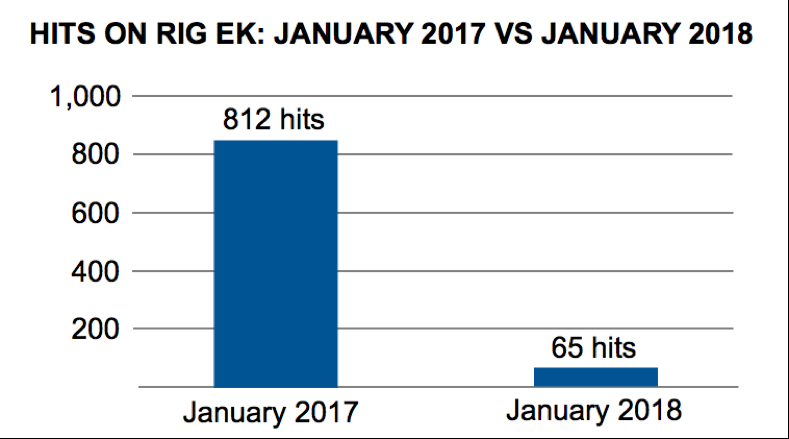 Figure 1: Hits on Rig EK in January 2017 versus January 2018.
Figure 1: Hits on Rig EK in January 2017 versus January 2018.
We have already discussed some reasons for this decline. Ultimately, the aftermath of criminal arrests combined with on-going vendor efforts to fortify browsers and browser-based applications have resulted in a cumulative effect devastating to EK developers. Criminal groups have shifted their efforts to other types of exploits like those targeting Microsoft Office vulnerabilities. And criminals have also turned their focus to social engineering schemes.
Payloads: From Ransomware to Coin Miners & Info Stealers
In January of 2017, Rig EK was primarily used to send different types of ransomware. The Afraidgate campaign used Rig EK to distribute Locky ransomware. The EITest campaign used Rig EK to distribute CrytoMix, CryptoShield and Spora ransomware. The pseudo-Darkleech campaign used Rig EK to distribute Cerber ransomware. Appendix A lists 39 reports documenting Rig EK used by various campaigns. 36 of these examples involve ransomware (the other three were Dreambot, Madness DDoS botnet malware, and NanoCore RAT).
How dramatic is the change in payloads distributed through Rig EK in January 2018 compared to January 2017? In general terms, ransomware is nearly out, while cryptocurrency miners (coin miners) and information stealers are in.
None of the ransomware we saw being distributed using Rig EK in January 2017 was being distributed in 2018. Cerber, CryptoMix, CryptoShield, Locky, and Spora are no longer active. In some cases, their development has forked into newer variants now distributed on a much smaller scale, such as a Cerber variant called Mangiber.
Similarly, none of the campaigns we saw pushing ransomware in January 2017 were doing so in January 2018. The Afraidgate and pseudo-Darkleech campaigns disappeared by May 2017. Criminals behind the EITest campaign are still active, but they stopped using Rig EK and have turned to social engineering methods like fake browser plugins and tech support scams.
In January 2018, Rig EK was used by at least three identifiable campaigns: Fobos, Ngay, and Seamless.
Fobos has used Rig EK to distribute the Bunitu proxy Trojan. Ngay has distributed coin miners and information stealing malware. Seamless has mainly distributed an information stealing Trojan named Ramnit.
Researchers have already reported the Ngay campaign distributing coin mining malware using Rig EK, but we have also seen Ngay using Rig EK to distribute the Remcos remote access tool (RAT). Ngay was first documented in December 2017. Since that time, it pushed Monero (XMR) coin mining malware. However, by January 19th, Ngay was pushing the Remcos remote access tool (RAT). Remcos RAT also has a keylogging component that steals information.
Except for four days in January 2018, Seamless continued to push the Ramnit banking Trojan, and the campaign has been using Rig EK to distribute Ramnit since March 2017. Ramnit is a banking Trojan that also behaves like an information stealer by retrieving passwords from browsers and other applications on the infected Windows host.
One small anomaly we saw with the Seamless campaign in January 2018 was from the 26th through the 29th. During that four day window, Seamless used Rig EK to push GandCrab ransomware, then it went back to pushing Ramnit.
Unfortunately, due to the way Rig EK encrypts its payload, we cannot use AutoFocus to identify Rig EK payloads. Appendix B lists 20 publicly-available reports in January 2018 that document Rig EK used by various campaigns to push information stealers like Ramnit and Remcos RAT, coin miners, and GandCrab ransomware.
The most interesting aspect of Rig EK payloads is the rise of coin mining malware. While we cannot use AutoFocus to find Rig EK payloads, we can certainly use it to find various coin mining malware. Using AutoFocus to search for various coin miners in January 2017 returned 2,368 unique samples. For January 2018, AutoFocus shows 65,512 samples using the same search criteria. That represents a 2,766 percent increase in coin miner samples from January 2017 to January 2018.
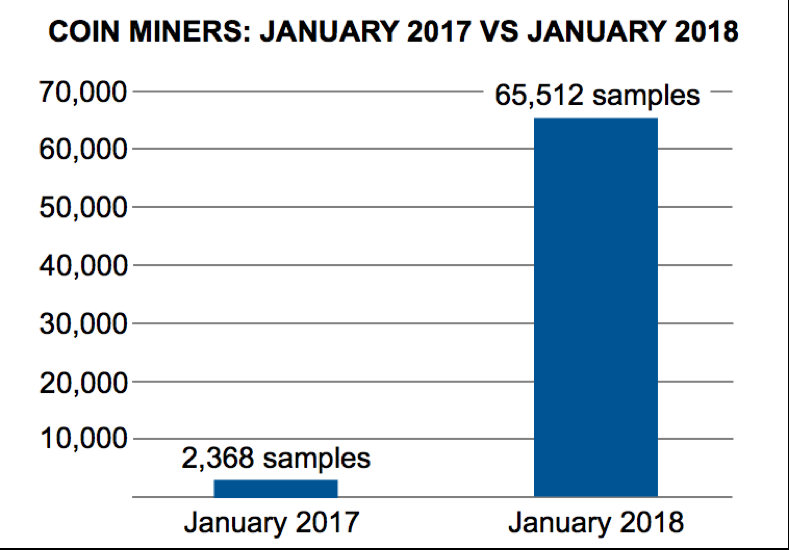 Figure 2: Coin miner samples in January 2017 versus January 2018.
Figure 2: Coin miner samples in January 2017 versus January 2018.
This dramatic increase in coin mining malware is reflected in public reporting of Rig EK, and we expect to see more coin mining malware as 2018 progresses.
Network Traffic: From Domains to IPs
In January 2017, Rig EK continued its well-established practice of domain shadowing for servers hosting the EK. Domain shadowing is used to frequently change domain names in an effort to avoid detection. However, in January 2018, Rig EK no longer uses domain names. Instead, it uses IP addresses to identify it EK servers, a practice that started in June 2017 in response to a coordinated effort documented by RSA Research that took down the associated domain shadowing infrastructure.
What else is different with Rig EK network traffic?
Other than IP addresses instead of domain names, Rig EK traffic is relatively unchanged a year later. The URL patterns are somewhat changed, but still recognizably Rig EK. In January 2017, Rig EK URL patterns contained recognizable English words. In January 2018, these English words have been replaced with Base64-encoded strings. See the images below for examples.
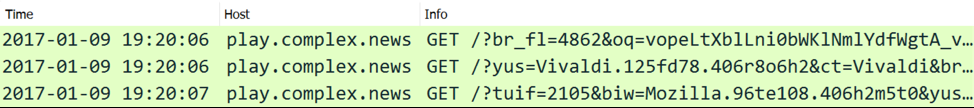
Figure 3: Example of URLs from Rig EK in January 2017.
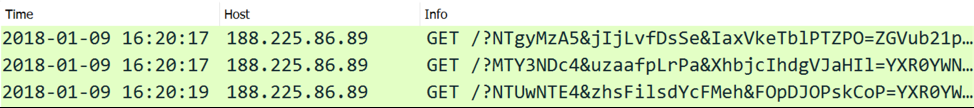
Figure 4: Example of URLs from Rig EK in January 2018.
These URL pattern changes indicate Rig EK is still trying to avoid detection. However, the loss of its domain shadowing infrastructure makes Rig EK at least as identifiable now as it was a year ago.
Conclusion
When we compare Rig EK in January 2017 with Rig EK in January 2018, the contrast is indeed striking. Rig EK is now distributing a much different selection of malware. Campaigns using Rig EK have mostly forsaken ransomware and now focus more on coin miners. Rig EK is still readily recognizable, but it is a much-reduced presence in our current threat landscape.
Palo Alto Networks customers remain protected from this threat. Our threat prevention platform applies IP signatures that easily detect current Rig EK URL patterns and enforce protections as necessary. AutoFocus users can track detected Rig EK activity using the RigEKFlashContainer tag.
We will continue to investigate this activity for applicable indicators to further inform the community and enhance our threat prevention platform.
Appendix A
Rig EK examples in January 2017:
2017-01-01 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-02 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-03 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-04 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-05 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-06 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-09 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-09 - unspecified campaign Rig EK sends NanoCore RAT and other malware
2017-01-10 - EITest campaign Rig EK sends CryptoMix ransomware
2017-01-11 - pseudo-Darkleech campaign sends Cerber ransomware and EITest campaign Rig EK sends CryptoMix ransomware
2017-01-12 - EITest campaign Rig EK sends CryptoMix ransomware
2017-01-12 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-13 - EITest campaign Rig EK sends CryptoMix ransomware
2017-01-13 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-13 - Afraidgate campaign Rig EK sends Locky ransomware
2017-01-14 - Afraidgate campaign Rig EK sends Godzilla loader for Locky ransomware
2017-01-15 - EITest campaign Rig EK sends CryptoMix ransomware
2017-01-15 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-17 - EITest campaign Rig EK sends Spora ransomware
2017-01-18 - pseudo-Darkleech campaign Rig EK sends Madness DDoS botnet malware
2017-01-18 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-19 - EITest campaign Rig EK sends Cerber ransomware
2017-01-19 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-19 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-20 - EITest campaign Rig EK sends Cerber ransomware
2017-01-21 - unspecified campaign Rig EK sends Spora ransomware
2017-01-22 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-23 - EITest campaign Rig EK sends CryptoMix ransomware
2017-01-24 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-24 - EITest campaign Rig EK sends CryptoMix ransomware
2017-01-25 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-26 - Afraidgate campaign Rig EK sends Godzilla Loader and Locky ransomware
2017-01-26 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-27 - Afraidgate campaign Rig EK sends Locky ransomware or Madness DDos botnet malware
2017-01-29 - unspecified campaign Rig EK sends Dreambot
2017-01-30 - Afraidgate campaign Rig EK sends Locky ransomware
2017-01-30 - pseudo-Darkleech campaign Rig EK sends Cerber ransomware
2017-01-31 - EITest campaign Rig EK sends CryptoShield ransomware (update to CryptoMix ransomware)
2017-01-31 - EITest campaign Rig EK sends CryptoShield ransomware
Appendix B
Rig EK examples in January 2018:
2018-01-01 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-09 - Rig EK campaign gets deep into crypto craze
2018-01-09 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-09 - Ngay campaign Rig EK sends Smoke Loader for Monero coin miner
2018-01-09 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-09 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-11 - Ngay campaign Rig EK sends Smoke Loader for Monero coin miner
2018-01-12 - Ngay campaign Rig EK sends Smoke Loader for Monero coin miner
2018-01-14 - Ngay campaign Rig EK sends Monero coin miner
2018-01-14 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-15 - Ngay campaign Rig EK sends Monero coin miner
2018-01-15 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-16 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-17 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-19 - Ngay campaign Rig EK sends Remcos RAT
2018-01-25 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-26 - Seamless campaign Rig EK sends GandCrab ransomware
2018-01-29 - Three days of Seamless campaign Rig EK pushing GandCrab ransomware
2018-01-30 - Seamless campaign Rig EK sends Ramnit banking Trojan
2018-01-31 - Fobos campaign Rig EK sends Bunitu proxy trojan
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
