This post is also available in: 日本語 (Japanese)
The Latin America (LATAM) region is geographically large and diverse, stretching from the northern border of Mexico to the southern tip of South America. It is also one of the fastest growing and largest regions of Internet users, recently surpassing North America (NAM) in sheer volume of users with Internet access. In just the last few years, the region has experienced an explosive growth in the number of users going online, and with it we’ve seen a similar expansion in the potential challenges that accompany growth. This blog discusses the threat trends Unit 42 has observed from July until December of 2016 in LATAM.
High Level Trends in the Second Half of 2016
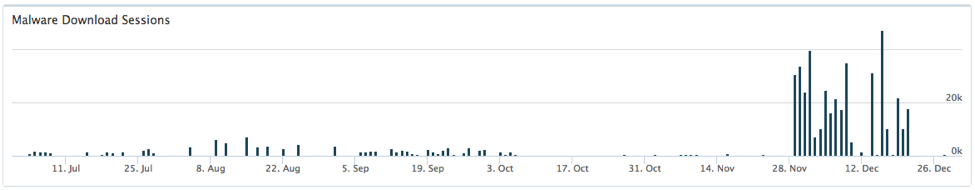
From July 1, 2016 through December 31, 2016, we observed nearly 530,000 unique sessions of unknown malware in the LATAM region, across more than 37,000 unique malware samples. 89% of the malware we observed was delivered via email phishing and the large majority was the ransomware variant known as Locky. Locky is a well-known and widely used ransomware variant first discovered in February 2016. Locky can be particularly dangerous as it uses public-private key infrastructure (PKI) for encryption and is also constantly evolving to evade security controls. It was the first ransomware variant to be found using malicious macros for delivery, leveraging specific evasion techniques, using exploit kits for delivery, and more recently, using various forms of script files as a delivery vehicle.
Interestingly, as we look at the distribution of malware sessions across the time frame, we see a significant flat-lining of malware sessions beginning October 7 through November 28.
This coincides with global observations of major Locky operator affiliates going offline on October 7, and slowly returning over the course of the month of November. Entering into late November through most of December however, we observed a massive increase in the amount of malicious activity across the LATAM region. Around late December around Christmas, we see another significant drop off in activity, likely due to a combination of less user interaction due to holidays as well as criminal operators potentially taking a holiday break themselves.
Additionally, in the month of September, we observed significant malicious activity involving the Bayrob Trojan. The Bayrob Trojan is fairly old, first discovered in 2007. The malware allows the operators complete access to the infected host, to perform such activity as harvesting personal information such as credit card numbers, to even allowing the operators to use the infected host to mine cryptocurrency. The observed activity spanned all across the LATAM region, but abruptly halted at the end of September. In December 2016, it was reported that the United States Department of Justice had extradited and charged three Romanian nationals in connection to Bayrob operation.
LAZARUS GROUP ATTACKS IN LATAM
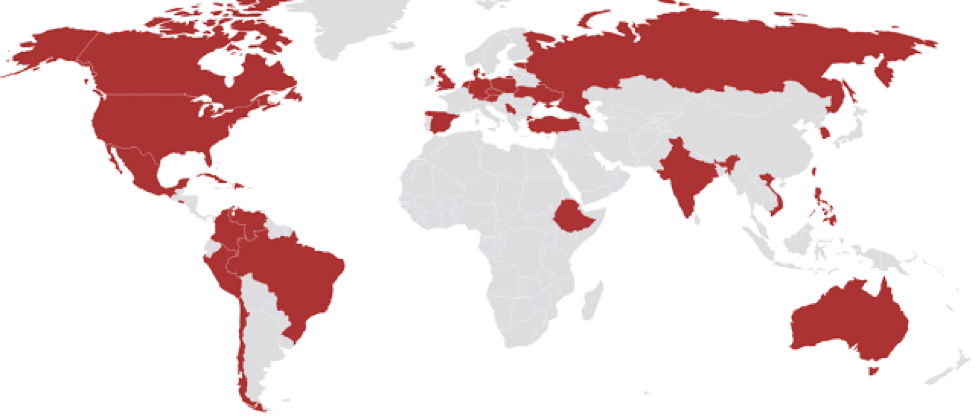
Recently, several reports were published regarding a series of attacks occurring in the October and November 2016 timeframe linked to an adversary group called the Lazarus Group. The Lazarus Group most recently is thought to have been linked a 2016 attack on the SWIFT payment system. These new series of attacks targeted financial institutions by modifying their websites to be used as watering holes. Initially, the attacks were thought to be limited in scope to a financial entity in Poland, but additional investigation rapidly identified two other financial institution websites in the LATAM region that had also been modified to be used as watering holes. The websites of the Comisión Nacional Bancaria y de Valores in Mexico as well as the Banco de la República Oriental del Uruguay in Uruguay were both identified to have been modified to redirect victims to a custom exploit kit targeting Adobe Flash and Microsoft Silverlight vulnerabilities. Even more interestingly, researchers identified an allowlist of targeted subnets within the exploit code and these included IP addresses from Mexico, Chile, Brazil, Peru, and Colombia as shown in Figure 1. The attack would only deliver malware if the target was within these allowlisted IP addresses.
Figure 1: Allowlisted Regions Source: BAE Systems
We believe the malware delivered by the exploit kit in this attack is a downloader tool previously associated with the Lazarus Group. This malware would allow the adversary to retrieve additional tools or perform other actions on the infected host. At this time, there has been no reports of stolen funds, although there is some reporting of large outbound data transfers from infected hosts.
MEXICO, BRAZIL, COLOMBIA, AND ARGENTINA
To better understand large scale threats that may be affecting the LATAM region, we will focus on four countries that our data showed experienced the most malware activity: Mexico, Brazil, Colombia, and Argentina.
MEXICO
Based on our data, 54% of the malicious activity we observed in the second half of 2016 in LATAM was in Mexico. The vast majority was malware delivered via email applications, but there was also a disproportionate amount of malicious activity occurring over FTP. While FTP was often abused in the past, today FTP is not a common network protocol leveraged by malware operators. In this case, from November 30 through December 5, we observed a significant outbreak of a malware variant known as Photominer.
Figure 2 Activity in Mexico 2016 H2
This malware was first discovered in June 2016 and its main purpose was to spread itself and mine a cryptocurrency called Monero on infected hosts. To accomplish its task of spreading and infecting additional hosts, Photominer has the capability of searching for insecure FTP servers to place itself on. After placing itself on an FTP server, it then searches for any possible websites hosted on the FTP server, and modifies the website to infect any unsuspecting visitors.
BRAZIL
31% of the malicious activity we observed in LATAM occurred in Brazil. The malicious activity we observed largely comprised of attacks involving Locky. Most of these attacks were sent via email applications, followed by simple web browsing by users. Locky activity alone generated over 70% of all malicious activity in Brazil based off our data.
Figure 3 Activity in Brazil 2016 H2
Outside of Locky activity, we began observing activity from a campaign we have called CerberSage Distribution towards the end of 2016. We’ve identified the CerberSage Distribution campaign as one that uses malicious Office documents to deliver Locky as well as two other ransomware, Cerber and Sage. Cerber is a widely available ransomware that is regularly updated and has a high success rate at encrypting hosts. Sage is a newer ransomware that behaves similar to other ransomware such as Locky or Cerber, but has an added ability to try and geolocate the victim as well as adding a persistence mechanism so that the infection starts every time the user logs into Windows. This tactic of using multiple kinds of ransomware in the CerberSage Distribution campaign may be used to expand the efficacy of infection using old, but reliable ransomware such as Locky while still being able to deliver newer variants with newer features such as Cerber or Sage in cases where Locky is ineffective.
COLOMBIA
Based on our analysis of data we found Colombia was one of the few countries not only in the LATAM region but also globally that was not dominated by Locky activity.
Figure 4 Activity in Colombia 2016 H2
Instead, the bulk of the malicious activity consisted of the Bayrob Trojan and a malware variant called PredatorPain. PredatorPain has been around since 2008 and is another widely available, low-cost malware tool that any criminal operator could have access to. It is an information stealing Trojan capable of capturing passwords, keystrokes, screenshots, and other sensitive information. The PredatorPain activity occurred in a single wave from November 30 through December 2 via a phishing attack using a purchase order subject line in English as the lure. The Bayrob activity also used email phishing as the delivery mechanism, and in general, email applications were used in the vast majority of malware related activity in Colombia.
ARGENTINA
Much like the rest of LATAM, Locky activity was dominant in Argentina, making up over 66% of all malicious activity observed in the country. Activity involving the Bayrob Trojan was also prominent. Together, they accounted for 98% of all malicious activity observed in Argentina from July 2016 through December 2016.
Figure 5 Activity in Argentina 2016 H2
Beyond the high volume of Locky and Bayrob activity however, several banking Trojans were also observed deployed against Argentinian targets. KINS, and Tinba, are banking Trojans whose objectives are to steal user credentials from financial institutions then siphon funds from the stolen accounts to their own accounts. KINS is a derivative of ZeuS, an older and well-known banking Trojan. KINS was created from the original leaked source code of ZeuS with minor, yet interesting changes increasing its capabilities. Tinba is now free due to its source code leaking in 2011. This makes it an attractive tool to use for many criminals. We also observed Pony, an older malware tool that has its source code available and remains very active. It was originally designed to steal user credentials, but is more often today used to retrieve additional malware once it has infected a host.
CONCLUSION
LATAM is a rapidly expanding region of Internet users that has no signs of slowing down. Criminals in particular seem to be quite aware of this phenomenon and appear to be treating the region as an emerging market to be leveraged. We know ransomware such as Locky has been largely victim-agnostic, but it has at times been questioned if certain regions might be more likely to pay a ransom versus others, which may lead to perhaps larger volume of attacks or more concentrated attacks against specific regions. The data collected and analyzed in this blog shows that this is unlikely to be the case, as ransomware activity appears to be just as voluminous in the LATAM region as any other region in the world.
The appearance of information stealers and banking Trojans activity is also interesting, as it may indicate that criminals have become aware of more users in LATAM using online banking and other online services in their everyday lives.
As the LATAM region continues to expand and develop, it is imperative that strong cybersecurity strategies are deployed throughout the region. Leveraging basic policies such as enforcing user privileges, blocking executable attachments in emails, and keeping applications patched can be extremely powerful in denying the adversaries their objectives. Pairing these policies with effective implementation of security technologies can further increase the efficacy of our strategies and allow us to maintain a strong security posture throughout the region.
Ignite '17 Security Conference: Vancouver, BC June 12–15, 2017
Ignite '17 Security Conference is a live, four-day conference designed for today’s security professionals. Hear from innovators and experts, gain real-world skills through hands-on sessions and interactive workshops, and find out how breach prevention is changing the security industry. Visit the Ignite website for more information on tracks, workshops and marquee sessions.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.