The ninth annual edition of Verizon’s Data Breach Investigations Report (DBIR) has just been released, and Palo Alto Networks is proud to have contributed data and analysis to help make the report as comprehensive as possible. Palo Alto Networks is committed to sharing threat intelligence across the security industry, exposing the evolving nature of threats, in order for organizations to better protect themselves.
This year we extracted a massive dataset from the AutoFocus threat intelligence service on over 38 million sessions carrying over 2.7 million unique malware samples. We worked with the Verizon team to add context to these samples with AutoFocus tag data, illuminating what campaign or family they were associated with.
Rapidly evolving malware
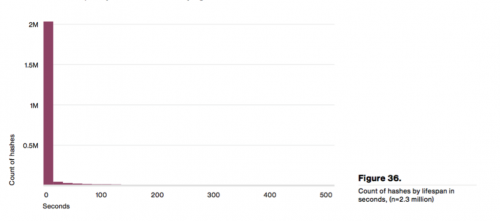
The DBIR team combined our data with intelligence collected from other contributors, coming to the conclusion that the life span of malicious samples is typically very low (i.e. samples are very rarely used more than a few times). The report found that "99% of malware hashes are only seen for 58 seconds or less," lending credence to the critical need for constantly updated protections deployed back to the network, lest organizations risk being infected by rapidly changing malware.
Shifts in Crimeware
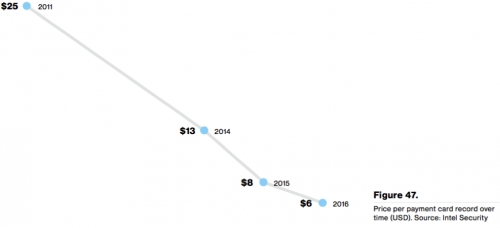
In many ways, this report suggests that the threat landscape has not shifted significantly from the 2015 report. However, it does present one compelling insight into the rise of a threat that is top of many people’s minds, ransomware. The graph below is the average price per payment card record in USD over the last 5 years (Source: Intel Security).
If you were a cyber criminal and had previously focused on stealing credit cards data with malware, the supply of new card numbers into the market in the last few years has made your life very hard. A 76% drop in the price of your offering over 5 years is devastating, and that might make you look for alternative ways to monetize the computers you infect with malware. This graph is a near inverse of the ramp we’ve seen in ransomware attacks between 2013 and today, adding more evidence to suggest cyber criminals may be abandoning certain forms of fraud to focus on their ransomware business model.
Overall, the 2016 DBIR underscores how time-tested techniques for infecting organizations continue to be responsible for the vast majority of breaches. While there may be shifts in monetizing attack, such as moving from stolen credit cards to holding machines for ransom, attackers continue to rely on their old tricks. Primarily motived by profit, we expect cyber attacks to continue going back to highly effective tactics like spearphishing or comprise by infected websites.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.