This post is also available in: 日本語 (Japanese)
In mid-April 2016, a campaign using Nuclear Exploit Kit (EK) to distribute Locky ransomware switched to using the Angler EK to install CryptXXX ransomware. This campaign uses gates registered through FreeDNS at afraid.org. We are calling this the Afraidgate campaign. Although we continue to see Locky distributed through malicious spam, we have not noticed Locky from EK traffic since mid-April.
An Evolving Campaign
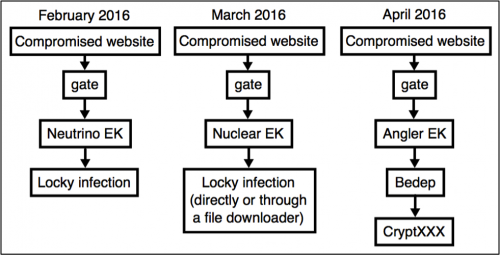
In March 2016, we observed Nuclear EK from the Afraidgate campaign spreading Locky ransomware. A consistent gate pattern in the infection chain pointed to the same campaign using Neutrino EK the previous month. Now this campaign points to Angler EK. Also with the change in EKs, the malware has switched from Locky to CryptXXX. Both of these malware families employ the ransomware business model, in which they encrypt a user’s files and demand a ransom in return for the decryption keys. The following chart illustrates the changes in this particular campaign:
Figure 1: Changes in EK and payload from the Afraidgate campaign.
The Angler/Bedep/CryptXXX Combo
In mid-April 2016, the pseudo-Darkleech campaign started delivering CryptXXX through Bedep from Angler EK. The same Angler EK/Bedep/CryptXXX combination has spread to the Afraidgate campaign, replacing Nuclear EK traffic used to deliver Locky.
Angler EK is a bit more advanced than Nuclear EK. Angler uses new exploits, usually before these exploits have made their way into Nuclear EK. When sending Bedep, Angler uses a "fileless" infection technique originally implemented in 2014. Bedep is installed without creating any files because it is loaded directly into memory by the exploit shellcode.
Bedep is a file downloader that infects the host with other malware. In addition to CryptXXX, Bedep also installs click-fraud malware. Recent updates to Bedep make it harder to use virtual machines (VMs) to investigate this malware. Bedep acts differently if it detects a VM. It will not download CryptXXX, and post-infection click-fraud traffic is different than seen from a normal physical host.
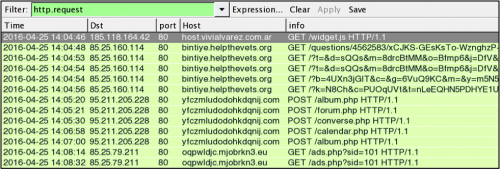
Figure 2: VM infection shows different post-infection traffic than the other examples here.
Three examples of Angler/Bedep/CryptXXX infection traffic from the Afraidgate campaign are shown below.
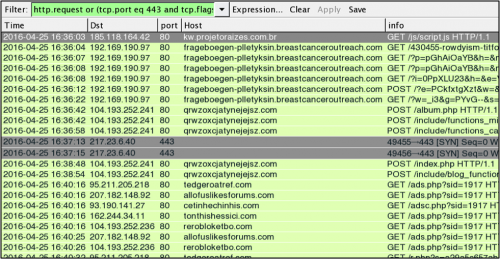
Figure 3: Gate on 185.118.164.42 leads to Angler EK/Bedep/CryptXXX on Friday 2016-04-22.
Figure 4: Similar gate on 185.118.164.42 leads to more Angler EK traffic on Monday 2016-04-25.
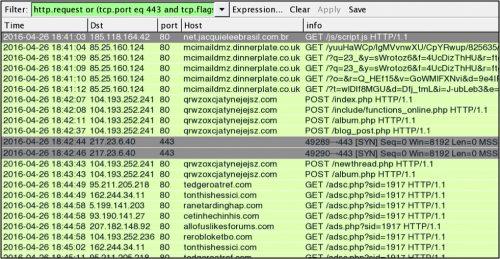
Figure 5: Similar gate on 185.118.164.42 leads to more Angler EK on Tuesday 2016-04-26.
Conclusion
CryptXXX is now the default ransomware deployed in at least two major EK campaigns and should be considered a growing cybersecurity threat.
Domains, IP addresses, and other indicators associated with Angler EK, Bedep, and CryptXXX are constantly changing. We continue to investigate this activity for applicable indicators to inform the community and further enhance our threat prevention platform.
WildFire continues to detect submitted .dll samples of CryptXXX ransomware, and AutoFocus identifies this threat under the Unit 42 CryptXXX tag.
Indicators of Compromise
As of Tuesday 2016-04-26, we have seen the following indicators of compromise associated with this campaign:
Gates used in this campaign:
- 185.118.164.42 port 80 - host.vivialvarez.com[.]ar - GET /widget.js
- 185.118.164.42 port 80 - kw.projetoraizes.com[.]br - GET /js/script.js
- 185.118.164.42 port 80 - net.jacquieleebrasil.com[.]br - GET /js/script.js
Angler EK:
- 85.25.160.124 port 80 - bintiye.helpthevets[.]org
- 85.25.160.124 port 80 - mcimaildmz.dinnerplate.co[.]uk
- 192.169.189.167 port 80 - candidulumbestuurlijk.newlandsierrarealestate[.]com
- 192.169.190.97 port 80 - frageboegen-plletyksin.breastcanceroutreach[.]com
- 192.169.190.97 port 80 - reikleivn-azarashi.orlandohomesbydevito[.]com
- 209.126.120.8 port 80 - litigators.esteroscreen[.]com
Bedep post-infection traffic:
- 104.193.252.241 port 80 - qrwzoxcjatynejejsz[.]com
- 95.211.205.228 port 80 - yfczmludodohkdqnij[.]com (using a VM)
Click-fraud traffic:
- 5.199.141.203 port 80 - ranetardinghap[.]com
- 93.190.141.27 port 80 - cetinhechinhis[.]com
- 95.211.205.218 port 80 - tedgeroatref[.]com
- 104.193.252.236 port 80 - rerobloketbo[.]com
- 162.244.34.11 port 80 - tonthishessici[.]com
- 207.182.148.92 port 80 - allofuslikesforums[.]com
- 85.25.79.211 port 80 - oqpwldjc.mjobrkn3[.]eu (using a VM)
CryptXXX post-infection traffic:
- 217.23.6.40 port 443 (custom encoding)
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.